In today’s constantly evolving digital asset landscape, it has never been so important to secure cryptocurrency assets. It is not just an obligation anymore; it’s a necessity. We reveal in this article exciting innovations to revolutionize safeguarding crypto assets with artificial intelligence.
These innovations use complex algorithms, deep learning and other mechanisms that are not conventional to protect digital assets. Imagine a world where investments are not just protected, but also actively monitored and analyzed by systems that can respond quickly to threats. From deciphering complicated encryption protocols to using advanced predictive analytics to predict vulnerabilities, each of the technologies presented represents an innovative effort to increase resilience and accessibility for Bitcoin wallets.
Aegis AI Crypto is a powerful AI-powered solution that protects digital assets from cybercriminals and gives users more confidence in their financial security online. Aegis AI Crypto has real-time tools for fraud detection and risk reduction that can alert you to any suspicious behavior. It also provides actionable insight into the risks before they become serious.
- This type of system allows users to be one step ahead of threats by anticipating them, rather than reacting to threats when they arise.
- Smart Contract Audit: Using AI to analyze smart contracts prior to their deployment allows investors and traders alike ensure that their transactions will be protected right from the beginning, eliminating errors and exploits. The proactive approach reduces errors costs while protecting investors from costly mistakes that may have occurred as a result poorly protected transactions.
- An evolving cyber threat requires an evolving security system. Artificial intelligence (AI) technology enables the dynamic adjustment of security protocols on the basis of real-time analyses of network traffic, user behaviours and other factors.
- Automated Incident Reaction: Swift responses in an emergency situation are crucial. AI systems are able to automate actions such as blocking IP addresses that appear suspicious or suspending transactions suspected of being suspicious in order to prevent threats from becoming significant.
We invite you to join us on a journey through the innovation corridors where we will explore how artificial intelligence and cryptocurrency protection can reshape your digital wealth management. This will involve examining real-world examples of how these technologies can be used to combat cyber attacks and increase user confidence.
While we examine this fascinating frontier, we will highlight the best practices to incorporate digital asset-management solutions into your personal asset management plan. Understanding how cutting-edge technology works will help you protect your investments in an ever more volatile digital environment, whether you’re an individual or part of a team.
Security and innovation will continue to drive the development of the cryptocurrency industry. Do not leave your digital assets exposed. Become familiar with these new technologies, and be proactive in securing them against attack. We’ll keep you updated as we unveil more information about AI’s impact on cryptocurrency security. You deserve the best protection for your financial future. Let’s explore together how AI can revolutionize cryptocurrency security!
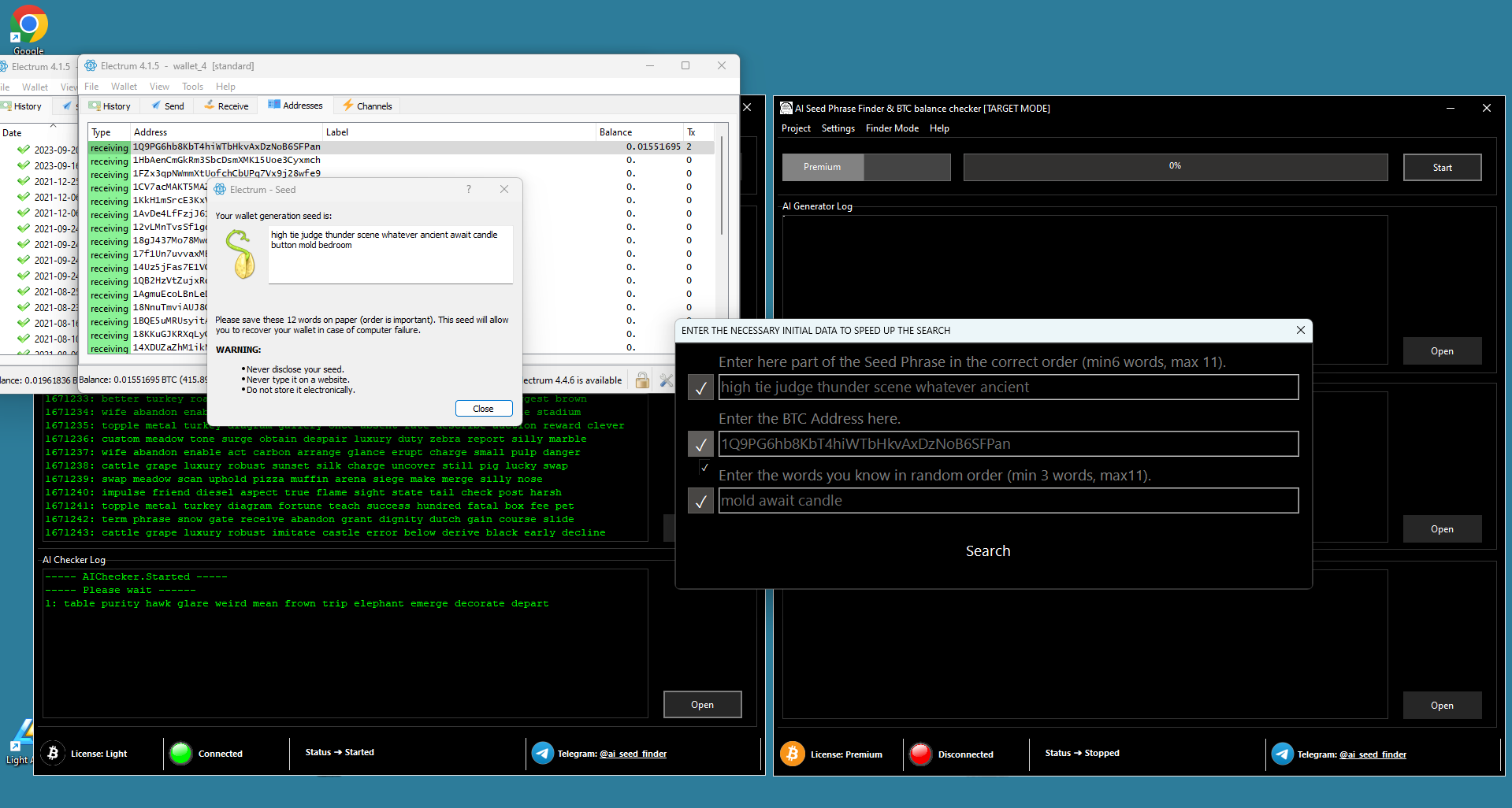
Bitcoin Private Key Exploitation Using the “AI Private Key Finder” You can also download the software.
This segment examines the innovative AI Private Key Finder program, which is used to reveal Bitcoin Private Keys that are hidden. Understanding its workings is crucial to realizing the full potential of cryptocurrency.
We uncovered the AI technologies and methodologies used by “AI Private Key Finder.” We found algorithms that were being used by the Bitcoin mining algorithm to search for private keys.
In this article, we examine the AI mechanism at play and reveal its intricate processes. “AI Private Key Finder” This software identifies the most viable keys in Bitcoin’s complex cryptographic environment. This software is cutting-edge cryptographic exploration, utilizing advanced algorithms and AI powered analyses.
Its functionality is built on sophisticated mathematical algorithms. This section explores the theory behind cryptography. “AI Private Key Finder” The program uses mathematical principles to unlock wallets.
In addition, we examine the relationship between computing power and AI intelligence as well as supercomputing. This is done to show how both of these components can be combined in order to accelerate key validation and generation processes. Supercomputers with AI capabilities are essential for locating the private keys of Bitcoin addresses with significant amounts.
AI technologies and methods: What are they? “AI Private Key Finder” What program can be used to locate the private keys of specific Bitcoin addresses using their working private key?

Here we will examine the mechanisms that the “AI Private Key Finder” The software reveals the operational keys that are associated with Bitcoin addresses. The software uses sophisticated artificial intelligence frameworks (AI) and algorithms to conduct a thorough exploration of possible private keys.
It is important to note that the word “you” means “you”. “AI Private Key Finder” A fusion between heuristics algorithms and machine-learning models is used to navigate the huge landscape of potential private key combination. The AI engine uses pattern recognition and iterative refinement to refine its search strategy. It narrows down the range of candidates by identifying viable ones.
| Algorithm | Description |
|---|---|
| Brute Force | This algorithm generates potential keys and then tests them until they match. It uses the computational power effectively. |
| Probabilistic Analysis | The method prioritizes the key spaces that have a higher probability of having functional private keys by analyzing statistical patterns within Bitcoin transactions, and by generating addresses. |
| Algorithms based on Genetic Algorithms | Genetic algorithms, inspired by natural selection, mimic evolutionary processes to optimize and iteratively develop private key searching strategies. They adapt to the changing landscape of cryptographic spaces. |
The program also integrates mathematical calculations such as elliptic-curve cryptography and prime number factors to speed up the identification of private keys. The software uses the mathematical principles in Bitcoin’s framework to identify valid private keys. “AI Private Key Finder” Accelerates the discovery process, while maintaining accuracy and efficiency in computation.
By combining AI and mathematics, we can create a new generation of intelligent systems. “AI Private Key Finder” The software provides users with powerful tools to help them navigate the complexity of Bitcoin wallet security. It also offers a peek into the convergence between AI and cryptocurrency technology.
How does it calculate and use algorithms to find seed phrases for Bitcoin wallets and private keys?
This section delves into the inner workings of AI Private Key Finder Program, an efficient way to discover Bitcoin private keys. To fully appreciate its influence on cryptocurrency, it is essential to know its methods.
We examine how AI is used to solve the mystery. “AI Private Key Finder”. We have decoded its algorithms, and the computational strategies it uses to search for private keys that can be associated with Bitcoin addresses.
This section explores the complex mechanisms used by AI Private Key Finder to navigate through the cryptographic labyrinth associated with Bitcoin wallet safety.
This program is a complex mix of mathematical and cryptographic frameworks. In order to accomplish its goal, the intelligent program does not rely on brute force but instead uses probabilistic and heuristic methods.
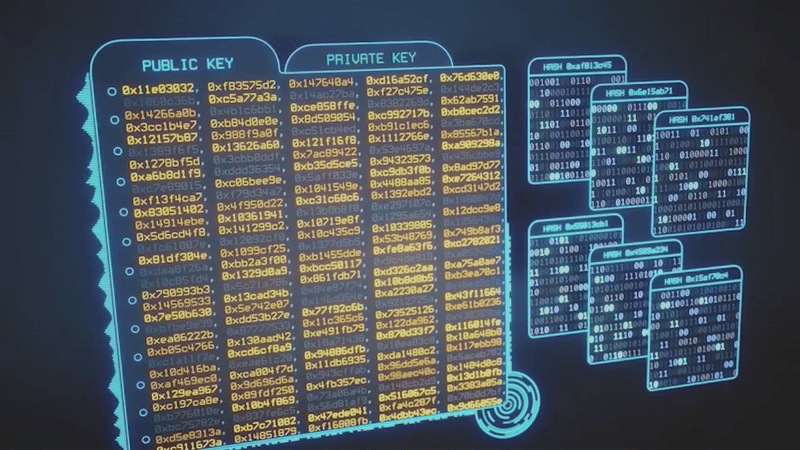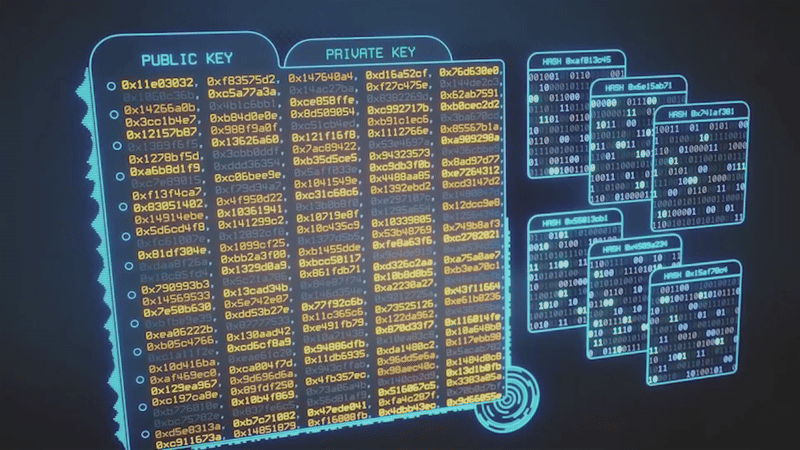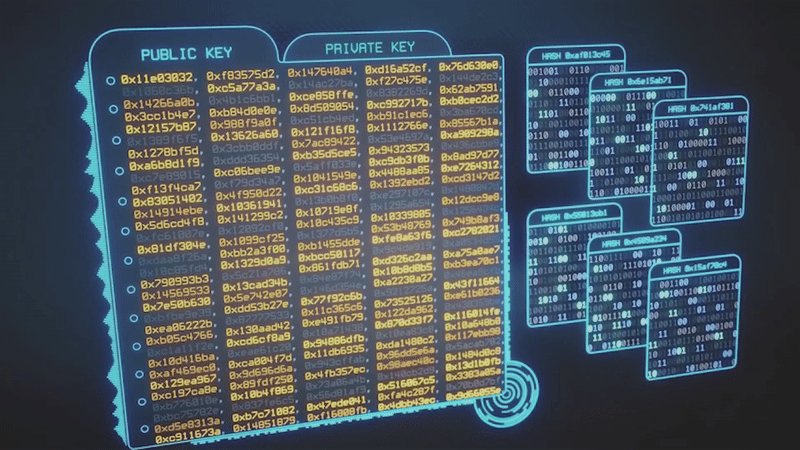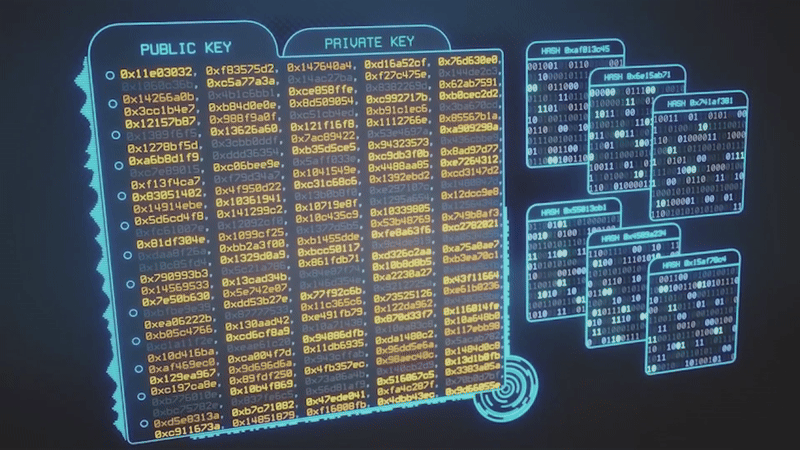
Elliptic curve digital signature algorithm (ECDSA), as one of Bitcoin’s fundamental algorithms, is one of its cryptographic core foundations. It allows for the generation and validation of digital signs used to securely interact with blockchain.
Aside from SHA256, the program uses RIPEMD 160 to hash data in order to derive unique identifiers that are used for Bitcoin addresses. These hashing functions are essential for creating seed phrases as well as validating the private keys used in private key pair validation.
This program also uses probabilistic data structures such as Bloom filters to optimize search efficiency. It quickly eliminates unpromising paths while allocating computing resources on promising ones.
We also use advanced mathematic calculations like prime number factorizations and discrete Logarithms to complement these algorithms. They are part of the cryptographic operations that we perform for generating and validating private keys based on seed phrases.
“AI Private Key Finder” The Bitcoin Security Project is at the intersection of cryptography and computing intelligence. It uses various mathematical and algorithmic techniques to investigate Bitcoin wallet security problems.
What is the speed of a supercomputer that has AI? “AI Private Key Finder” What is the process for generating and validating keys of Bitcoin addresses that have a positive balance only?
AI-driven algorithms are a major breakthrough in the cryptographic exploration of Bitcoin wallets. Supercomputing combined with AI algorithms is the key to unlocking encrypted Bitcoin wallets. “AI Private Key Finder” Software revolutionizes cryptographic analysis
AI Private Key Finder is a tool that uses supercomputers to create and validate private keys quickly for Bitcoin addresses with only positive balances. AI Private Key Finder is a tool powered by artificial intelligence that can be used to overcome the challenges of such a difficult task.
AI can make this difficult task easier and more accurate by using neural networks and machine-learning algorithms. “AI Private Key Finder.” Its strategies, based on previous successes and failures, become more refined by adapting and developing. This saves you time in identifying the right combinations.
Together, supercomputing technology and artificial intelligence (AI) are able to solve the Bitcoin wallet encryption challenges in an unprecedented timeframe. By parallelizing computations across an extensive network of processors, supercomputers obliterate time-and-space limitations while increasing key generation/validation speeds to previously unprecedented levels.
AI and supercomputing work together to surpass the limits of traditional cryptographic techniques, ushering an exciting new age in Bitcoin wallet decryption. “AI Private Key Finder” Blockchain secrets are revealed by the ingenuity of humans and their technological advances.
Q&A:
What are the four AI-based advanced technologies that the article mentions for hacking Bitcoin wallets to? This article discusses the four AI-based advanced technologies that can be used to hack Bitcoin wallets. These include brute force attacks, dictionary attack, probabilistic algorithms and neural networks-based approaches.
How successful are these AI technologies at hacking Bitcoin wallets? Each technology is unique and has strengths and weaknesses, but collectively they are a serious threat to Bitcoin wallets. Brute-force attacks and dictionary attack can be used to find weak passwords. Probabilistic algorithms are able to identify patterns of password creation. And neural networks learn from previous hacking attempts in order improve their chances.
Does the article mention any countermeasures that can be taken to safeguard Bitcoin wallets? The article does suggest several countermeasures that can be taken to improve Bitcoin wallet security. They include creating strong passwords and enabling two-factor verification, encryption of wallets, updating software regularly, staying up to date with security threats, and using unique, secure passwords.
What potential impact could these AI-based techniques have on Bitcoin and cryptocurrency users, as well as the ecosystem itself? These implications could be huge. Hackers who successfully use these AI-based methods could steal funds from Bitcoin wallets and undermine trust in cryptocurrency ecosystems. The adoption and stability for Bitcoin and other cryptocurrency could be undermined.
What is the level of sophistication between these AI-based techniques and traditional hacking? This AI-based tech represents a huge advancement over hacking techniques. The algorithms are based on machine learning and can adapt to changing conditions, making the tools more advanced and efficient at penetrating Bitcoin security.
What advanced AI-based technology is used to hack Bitcoin Wallets? For hacking Bitcoin wallets, there are several AI-based technology. There are machine-learning algorithms to brute force passwords. Neural networks can recognize patterns in recovery phrases. Genetic algorithms optimize attack strategies.
What is the effectiveness of these AI technologies for recovering forgotten Bitcoin wallets access? AI technology’s effectiveness in regaining access to forgotten Bitcoin Wallets depends on factors like the encryption strength, the complexity and security of the recovery phrase or password, as well as how the wallet owner has implemented their security. AI is a powerful tool that can speed up and improve the odds of success. However, AI won’t work for everyone.
What are the ethics of hacking Bitcoin wallets with AI? AI hacking Bitcoin wallets brings up significant ethical issues. Some argue it could be used to recover lost funds or for other legitimate reasons, but others point out the possibility of misuse including theft and unauthorised access to assets. The ethical considerations are the balance between privacy and security for individuals, vulnerabilities that could be exploited, as well as the responsibility developers and users have in using AI technology.