The protection of digital assets depends on innovative measures between diligence and innovation within the decentralized finance world. Knowledge about cyber threats combined with reliable protection measures becomes necessary for ensuring digital asset security since their value attracts more sophisticated cybercriminals – all investors must remain alert and proactive to potential threats.
Several defensive measures must be applied to secure the digital fortress because it faces growing vulnerability to cyber threats. The protection of investments needs advanced encryption systems and authentication protocols that can detect new threats but this kind of technology remains unavailable at present. The implementation of proper strategies along with execution plans.
Strategies that enable users to control their digital wealth constitute the fundamental basis for protecting cybersecurity systems. With physical identifiers and distributed identity management solutions, users can obtain enhanced security by accessing their wallets through their vision and finger-based identification techniques which represent the upcoming standard of safe authorization processes. This solution provides both the ease of use and the highest possible defensive capabilities.
The protection of your assets requires knowledge about current threats present within digital financial business operations. The multitude of cybercriminal approaches includes malware that breaches systems as well as phishing scams which trick people into revealing sensitive data and ransomware threats that lock up your files until payment is made. The first step of defense starts with knowing about existing threats because this knowledge enables prompt action before dangers materialize.
Access Control represents an essential strategy which limits access to authorized personnel thus reducing unprechttp://www.hackread.com/attack-against-securing-childrens-education/edrenteries and unauthorized usage of assets.
Encryption software ensures vital protection of sensitive data through encryption which transforms information into indecipherable code for unauthorized users even when they obtain access to the data. This protection remains effective regardless of unauthorized access. Every organization that conducts periodic assessments through regular security audits detects weaknesses before exploitation so teams can fortify security measures ahead of possible cyber attacks. Your organization will gain improved speed to react to possible threats through the implementation of AI-powered detection systems for spotting anomalous activity.
The technology revolution in digital finance demands organizations build speed in their ability to detect upcoming threats. Secure record-keeping enabled by Blockchain immutability together with Machine Learning algorithms provides both early-breach detection and asset protection revolution through artificial intelligence.
A combination of strategy descriptions and successful case examples from individual and organizational cyber defense measures will be provided in this section.
The present situation in cryptocurrency space together with digital assets ownership requires investors and businesses to maintain the highest possible level of risk management. Your investment protection requires tools and strategies against cyber dangers and their related threats which knowledge will empower you to implement effectively. Our examination of this matter will begin now because your financial future depends on it so seize control of digital security right now.

Common Vulnerabilities in Bitcoin Wallets Vulnerable to Hacking Exploitation and Five Methods for Mitigating Them
The following part examines how Bitcoin wallets contain weaknesses that allow attackers to take advantage of them for theft. Protecting digital assets from improper access and theft requires proper knowledge of attackable Bitcoin wallet vulnerabilities.
- 1. The security foundation of Bitcoin wallets depends on seed phrases but incorrect seed generation or storage leads to potential wallet exploits. Users must generate their seed phrases through secure methods before maintaining them offline to avoid exploitation risks.
- 2. Bitcoin wallets that depend solely on passwords for security become vulnerable to brute force attacks because attackers find it tougher to access these wallets compared to MFA or complex unique passwords individually. MFA along with complex unique passwords represents a powerful defense system that protects wallets from unauthorized access attempts.
- 3. The digital signatures that control Bitcoin access need proper security because unprotected private keys located on insecure devices make these wallets attractive targets for hackers. Secure storage formats that include hardware wallets with encryption mechanisms enhance the protection measures for private keys.
- 4. Users face vulnerability from phishers who deceive victims through deceptive techniques like fraudulent emails and imitation websites to obtain sensitive information. People can protect themselves by checking email sources and website authenticity to avoid becoming victims of such fraudulent schemes.
- 5. Users who maintain outdated wallet software and firmware become exposed to known hacker exploits because they fail to implement necessary security patches from trusted developers.
Bitcoin users who employ preventive security protocols combined with vulnerability mitigation techniques will experience reduced unintended access threats to their digital resources in addition to defense against criminal attack.
Six Most Efficient Methods for Bitcoin Wallet Breaches via Seed Phrase and How to Mitigate Potential Vulnerabilities
The security of Bitcoin wallets stands vital in cryptocurrency protection because attackers persistently look for vulnerabilities to exploit seed phrase weaknesses. The following discussion examines six complex hacking methods that exploit seed phrases for wallet access and presents preventive measures as well as proactive countermeasures against wallet breaches.
The protection of Bitcoin wallets stands as the primary priority in cryptocurrency security operations. Attackers persistently try to discover security weaknesses because seed phrases present a significant vulnerability. We will analyze the six most effective hacking methods which target Bitcoin wallets through seed phrases followed by preventive measures against these attacks.
Attackers use Dictionary Attacks to systematically generate dictionary-based combinations which they use to guess Bitcoin wallet seed phrases. Sophisticated algorithms help hackers to instantly cycle through different permutations because human-generated phrases show predictable patterns.
Computing power serves as the basis for brute-force attacks since hackers attempt every potential sequence of words until they find the correct one. The method continues to pose a threat because hackers develop their hardware and software capabilities.
Social engineering attacks combined with phishing techniques are used by hackers to deceive users into giving away their seed phrases without their knowledge. Attackers deceive their victims through phishing emails together with fake websites and deceptive communications in order to steal sensitive information.
Keyloggers function as harmful software which stealthily records all key inputs from users. A device infection by hackers enables them to record seed phrase entries during typing so they can acquire Bitcoin wallet access without authorization.
The generation process of seed phrases contains weaknesses because certain wallet systems or platforms unintentionally create patterns or predictable sequences that hackers can exploit.
Security enhancement requires identifying all weaknesses before implementation of remedies.
The internal staff members who work for cryptocurrency companies become major security risks due to their position as insiders. The privileged access some individuals hold enables them to illegally obtain seed phrases because proper access controls and monitoring systems must exist for security purposes.
Strategic actions exist to substantially decrease the security risks which seed phrase vulnerabilities create.
The use of hardware wallets enhances security since seed phrases get saved offline which protects them from internet-based attacks:
- A multi-signature authentication system needs different signature approvals to validate transactions which enhances the security against unauthorized transaction attempts.
- The combination of alpha-numeric elements and symbols and capitalization patterns in strong passwords protects wallets from brute-force attacks.
- Security audits should happen regularly to inspect wallet security systems and detect weaknesses which require immediate solution updates.
The importance of seed phrase protection and social engineering defense needs to be taught to users through educational programs that foster their ability to stay alert during such threats.
A dual strategy of technical system strength and user education will enable people and organizations to create protective measures against seed phrase abuses which secures Bitcoin investments against malicious manipulation.
Criminal hackers perform dictionary attacks through Internet searches which generate complete seed phrase combinations that they use to try guessing Bitcoin wallet seed phrases. Hackers use advanced algorithms to perform quick permutations checks because human-generated text patterns allow them to exploit these predictable patterns.
Brute-force attackers use this approach during attacks to scan every possible word combination with all possible seeds and characters until they find a match despite their growing computational resources.
By employing social engineering methods hackers make users unintentionally give away their sensitive information through fake emails and sites and fake communications. Through phishing emails hackers seek to deceive innocent people into revealing their sensitive information before manipulation occurs.
Keylogger software acts as malicious software which records all user keystrokes without user detection. Attackers use Keylogger software to break into their target device and use the obtained keystrokes to access Bitcoin wallets illegally.
Some seed phrase generation systems in Bitcoin wallets and platforms contain predictable vulnerabilities that hackers can exploit through their flawed processes. Security enhancement requires the identification and correction of such system weaknesses.
The privileged access of cryptocurrency firms employees creates a direct security threat because they can illegally access seed phrases which demonstrates why secure access management systems must be implemented for monitoring purposes.
Multiple precautions exist that can substantially lower the security risks stemming from seed phrase vulnerabilities
- Companies should invest in hardware wallets since these devices store seed phrases securely offline and reduce the chance of online assaults.
- Multi-Sig Authentication establishes an authorization system requiring several signatures for clearing transactions which enhances system-wide protection.
- A robust password defense system can be established through passwords that contain alphanumeric elements combined with symbols and both uppercase and lowercase letters.
- Wallet security protocols undergo regular evaluations which enables a prompt identification of vulnerabilities to prepare for needed security updates or patches.
- User education about seed phrase protection and social engineering threats will make them more cautious thus enabling them to stay alert against these types of attacks.
To defend against seed phrase-based attacks organizations together with individuals should implement an integrated approach which combines technical security systems with educational programs that teach users how to protect their Bitcoin holdings.

7 Progressive Methods for Hacking Bitcoin Addresses and How to Counter Them
In this section, we delve into the intricacies of breaching the security of Bitcoin addresses through innovative and evolving techniques. Understanding these methods is crucial for safeguarding your digital assets in the ever-evolving landscape of cyber threats.
- Exploiting weaknesses in cryptographic algorithms remains a primary avenue for hackers to compromise Bitcoin addresses. These vulnerabilities often stem from flaws in the encryption protocols utilized to generate private keys.
- The advent of quantum computing poses a significant threat to traditional cryptographic methods, including those used in Bitcoin wallets. Quantum computers have the potential to break current encryption standards, rendering private keys vulnerable to exploitation.
- Human error remains a critical factor in Bitcoin address security. Social engineering tactics, such as phishing scams and impersonation, are employed to deceive users into revealing their private keys or seed phrases, leading to unauthorized access.
- Malicious software, including keyloggers and remote access trojans (RATs), can compromise the security of Bitcoin wallets by covertly capturing private key information. These stealthy attacks often go undetected until significant damage has been done.
- Brute Force Bitcoin wallet attacks: Despite advancements in encryption, brute force attacks remain a persistent threat. Hackers employ powerful computing resources to systematically generate and test possible combinations of private keys until the correct one is discovered, allowing unauthorized access to Bitcoin addresses.
- Supply Chain Attacks: Targeting vulnerabilities in the supply chain presents another avenue for compromising Bitcoin address security. Attackers may exploit weaknesses in hardware wallets or compromise the integrity of software updates to gain unauthorized access to private keys.
- Blockchain Analysis: The transparent nature of the blockchain poses a unique challenge to Bitcoin security. Sophisticated analysis techniques can be used to trace transactions and identify patterns, potentially compromising the anonymity of Bitcoin users and their associated addresses.
To mitigate the risks posed by these progressive hacking methods, users must adopt a multi-layered approach to security. This includes implementing robust encryption standards, maintaining vigilance against social engineering tactics, utilizing reputable antivirus software to detect and remove malware, and staying informed about emerging threats in the cryptocurrency space.
Distinguishing Bitcoin Wallet Hacking from Recovery Using AI and Specialized Software Methods
In the realm of cryptocurrency security, the differentiation between Bitcoin Wallet Hacking and the subsequent recovery process via artificial intelligence (AI) and specialized software is pivotal. While hacking pertains to unauthorized access and exploitation of vulnerabilities within a wallet’s infrastructure, recovery involves employing innovative methodologies, including AI-driven algorithms and purpose-built software, to regain access to lost or compromised wallets.
Hacking Bitcoin wallet entails exploiting susceptibilities inherent in its design or implementation. This nefarious activity often involves sophisticated techniques such as brute-force attacks, where assailants employ relentless trial-and-error methods to guess private keys or seed phrases, and exploiting known vulnerabilities to gain unauthorized access to wallets and pilfer funds.
Specialized software together with AI forms recovery mechanisms which reduce the damage caused by lost or compromised access credentials. The methodologies utilize AI algorithms to predict possible seed phrases or private keys that belong to a certain wallet which helps users regain access to their funds through non-invasive means.
Hacking represents an unlawful attempt to breach Bitcoin wallet security yet recovery methods follow legitimate procedures to regain wallet access through modern technological methods which maintain security standards.
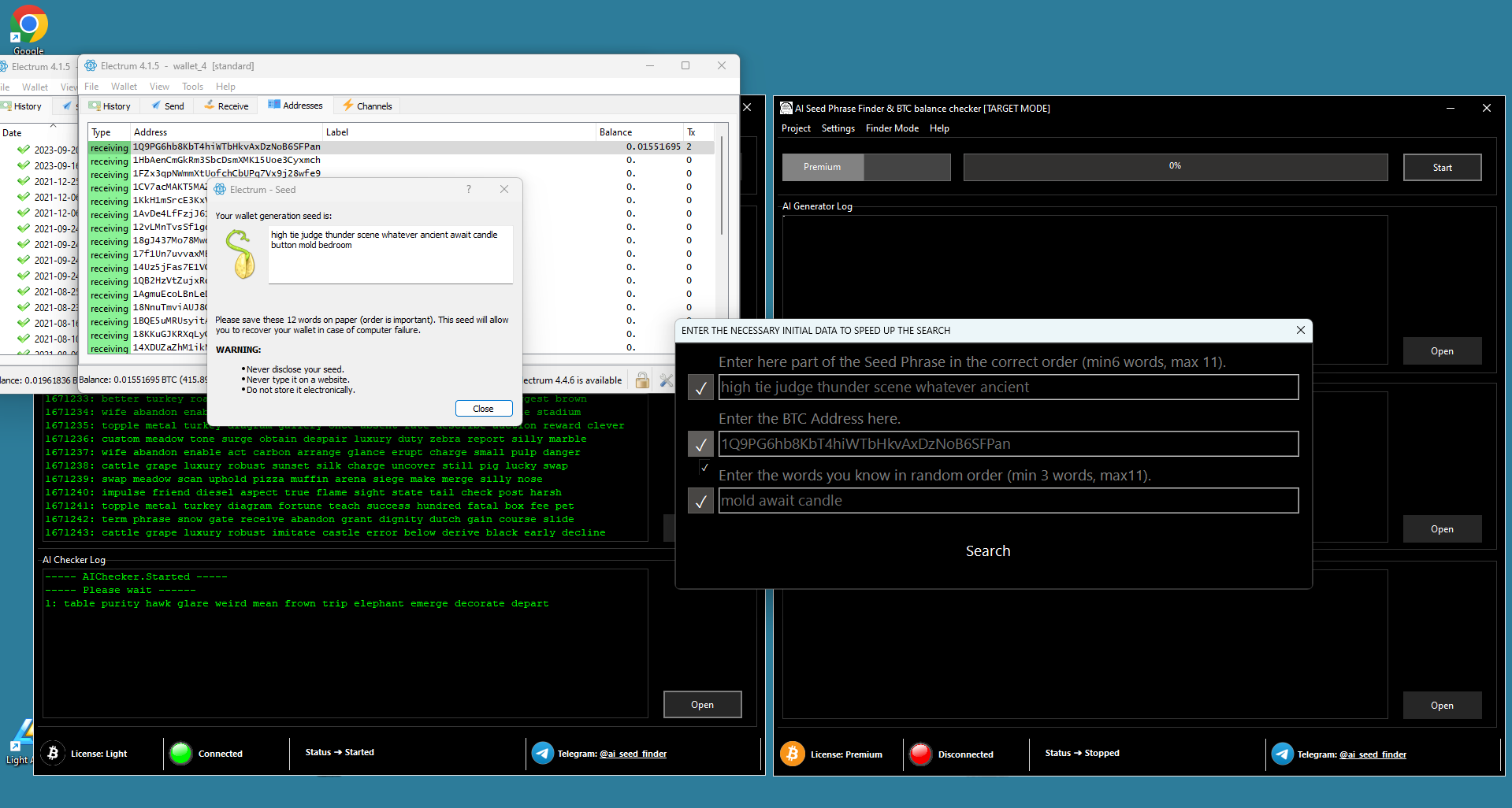
The software offers an AI Seed Phrase and Private Key Finder feature that utilizes AI technology with supercomputer computational power to identify bitcoin wallet and address keys swiftly.
The “AI Seed Phrase and Private Key Finder” software combines two essential functions by working as a hacking instrument while providing necessary help for Bitcoin wallet access. Through its use of advanced artificial intelligence algorithms connected to remote supercomputers the program identifies valid seed phrases and Bitcoin wallet private keys with fast speed to help users regain access.

| Aspect | Explanation | ||
| Algorithm Utilization | The program employs sophisticated mathematical and AI-driven methods to swiftly generate a multitude of seed phrases and private keys, significantly expediting the process of identifying the necessary access codes for Bitcoin wallets. | ||
| Mass Generation and Validation | Its core functionality involves mass generating seed phrases and private keys, followed by a meticulous validation process to ascertain their compatibility with specific Bitcoin wallets or addresses of interest to the user. | ||
| Positive Balance Identification | One of its distinctive features is the inclusion of a mode dedicated to mass generating seed phrases and private keys, subsequently cross-referencing them against addresses with positive balances. We delve into the intricate realm of the “AI seed phrase & Private Key Finder” program, a tool that straddles the line between potential ethical concerns and undeniable utility in the realm of Bitcoin security. This software, designed with a dual nature, poses a paradoxical question: is it a tool for hackers or a salvation for those who have lost access to their digital wealth?
What sets this program apart is its ability to harness the immense computational power of rented supercomputers, employing them remotely to expedite the search for valid seed phrases and private keys. This method, known as mass generation, involves the systematic creation of countless combinations followed by rigorous validation against specific Bitcoin wallets or addresses of interest to the user. Now, the crux of the matter lies in its dual functionality. On one hand, it raises ethical concerns as it can be perceived as a tool for potential malicious actors seeking unauthorized access to Bitcoin wallets. Yet, on the other hand, it serves as a lifeline for individuals grappling with the loss of their access credentials, offering a glimmer of hope in an otherwise dire situation.
Ultimately, the decision to utilize the “AI seed phrase & Private Key Finder” program rests on the delicate balance between its potential risks and undeniable benefits. While its capabilities may raise eyebrows in the cybersecurity community, its role as a beacon of hope for those facing Bitcoin wallet access issues cannot be overlooked. Exploring Mathematical and AI Methods Utilized by the “AI Seed Phrase & Private Key Finder” ProgramIn the quest for accessing Bitcoin wallets with positive balances, the “AI Seed Phrase & Private Key Finder” program employs sophisticated mathematical algorithms and artificial intelligence (AI) techniques. These methods are designed to swiftly generate a multitude of seed phrases and private keys, aiming to match them with specific Bitcoin wallets or addresses of interest to the user. The essence of the mass generation method lies in its ability to systematically produce numerous potential seed phrases and private keys, leveraging mathematical permutations and AI-driven optimizations. This process enables the program to explore vast combinations at an accelerated pace, significantly enhancing the probability of discovering valid access codes. Subsequently, the generated seed phrases and private keys undergo validation procedures to ascertain their relevance to the targeted Bitcoin wallets or addresses. This validation phase is crucial, ensuring that the identified codes possess the requisite attributes to unlock the desired wallets successfully. The validation process involves intricate comparisons and checks against the structure and cryptographic properties of Bitcoin wallets. Through meticulous analysis, the program verifies whether the generated seed phrases or private keys align with the expected format and cryptographic signatures associated with the target wallets. Upon successful validation, the program identifies the access codes that correspond to Bitcoin wallets holding positive balances. This capability is pivotal, as it enables users to gain entry to wallets containing valuable assets, facilitating their management and utilization. Overall, the “AI Seed Phrase & Private Key Finder” program employs a combination of mathematical algorithms and AI techniques to facilitate the rapid generation of seed phrases and private keys. Through meticulous validation processes, it ensures the identification of access codes pertinent to Bitcoin wallets with positive balances, offering users a valuable tool for accessing and managing their cryptocurrency assets. Detailed Explanation of the Mass Generation Mode in “AI Seed Phrase & Private Key Finder” ProgramThe “AI Seed Phrase & Private Key Finder” program contains essential security features because it enables users to generate seed phrases and private keys in bulk then verify these keys against addresses that hold positive balances. The section explains the reasons behind this feature as well as the operational process which enables access to Bitcoin wallets with exclusively positive balances. The mass generation mode in the program responds to the core difficulty experienced by cryptocurrency users who lose access to their seed phrases or private keys. The cryptographic elements function as digital keys that enable wallet access to Bitcoin funds contained in corresponding Bitcoin wallets. Users who cannot retrieve their seed phrases or private keys permanently lose control of their funds. The program contains a method which automatically produces and verifies potential access codes to assist users in recovering wallet control. The method starts with the program using mathematical algorithms and artificial intelligence for creating thousands of potential seed phrases and private keys. The system produces different code combinations which establish a complete range of potential Bitcoin wallet unlocking possibilities. The system executes a strict validation process on the previously generated codes. The validation phase functions as an essential step because it analyzes all produced codes to discover those which match Bitcoin addresses that hold funds. The validation method requires blockchain inquiries to check the balances linked to every generated address. The Bitcoin program uses blockchain ledger cross-referencing to detect positive balance addresses which indicate successful Bitcoin fund access. Accessing wallets containing funds holds the highest significance because it directly benefits users who wish to restore control of their assets. The program focuses on wallets containing funds because this enables users to retrieve assets currently present in the blockchain network. The program’s strategic design reduces wasted time on unproductive wallet access attempts which results in maximizing its usefulness for users. The security protocol uses mass generation of keys followed by validation against addresses that contain funds to provide users with a forward-thinking security approach. Through systematic access code exploration followed by wallet balance verification the “AI Seed Phrase & Private Key Finder” program gives users an efficient way to regain control of their digital assets. In considering the acquisition of the “AI Seed Phrase & Private Key Finder” program, it’s crucial to delve into the motivations driving potential users toward this software solution. Despite the significant expense associated with renting computational resources from a supercomputer, users are drawn to this tool for a variety of compelling reasons:
Ultimately, despite the financial investment required, the “AI Seed Phrase & Private Key Finder” program appeals to a diverse range of users, each motivated by unique objectives spanning from asset recovery and security enhancement to professional pursuits and intellectual curiosity. |
Advanced technology enables people to simplify their journey through digital financial systems. Protecting your digital wealth represents the top priority within the cryptocurrency domain because each trade produces more independence in financial management. A revolutionary strategy exists which allows digital currency recovery and enhances the protection of your digital assets from cyber threats.
New digital resilience emerges from the combination of innovation and security principles which lead us toward a modern digital future. Modern algorithms join forces with artificial intelligence to create a protection barrier for your virtual possessions against unauthorized intruders.
The disclosure of strategies for treasure retrieval and invulnerable cyber defenses will be your path to redemption and empowerment. The digital revolution brings every computer interaction under protective layers which secure your cryptocurrency ownership.
How Can I Safeguard My Bitcoin Wallet Seed Phrase From Intrusion by Utilizing Custom Words?
We will study methods for improving Bitcoin wallet seed phrase security through the addition of personalized word selections in this part. Digital asset defense needs advanced security methods above standard protocols since your seed phrase security will improve when you add unique elements reducing both unauthorized access and money loss.
Seed Phrase Protection works as the fundamental security element in Bitcoin wallet management because this phrase consists of words that allow fund access. To protect your security from brute force attacks you should strengthen the weak point with custom security terms because this addition creates multiple encryption layers which boost your protection against intruders.
The following strategies should be considered to protect your seed phrase security:
To achieve diversification in your seed phrase add personal terminology including important dates and specific names of meaningful people including hidden references exclusively known to you.
You can improve seed phrase confidentiality through obfuscation techniques by adding deliberate spelling mistakes and inconsistent capitalization which will make dictionary attacks more difficult.
Diversify your seed phrase encryption by separating it into parts with custom words between sections to prevent easy understanding as a whole message. Regular adjustments to your seed phrase custom words through rotation will stop unauthorized access attempts from succeeding.
Your Bitcoin wallet seed phrase protection against attacks grows stronger when you apply personalized words because it makes unauthorized access attempts less successful. You can defend yourself against cyber threats effectively while displaying a solid confidence level thanks to security-focused participation.
The correct method for storing Private Keys along with details about the dangerous nature of “Vanity BTC Address” technology for generating Bitcoin Addresses needs urgent attention
The security of private keys ranks as the prime cryptocurrency security issue both crypto investors and enthusiasts need to follow best practices in storage methods to minimize security risks of unwanted access and stolen assets.
Private keys function as the essential access points to cryptocurrency wallets and users must safely secure them for reliable protection. The accessibility system must guarantee trouble-free operations while asset management needs inclusion with defense capabilities to prevent loss and theft instances.
Various firms are utilizing physical wallets designed for private key storage as a secure system which remains separate from internet threats while protecting the stored keys from damage. Mnemonic Phrases (also known as seed phrases) serve as a dependable storage solution for private keys through their straightforward method of emergency private key retrieval. Secure storage of these phrases or memorization creates an efficient safety mechanism.
Cold storage solutions serve as protected private key storage systems which disconnect keys from internet access thus protecting them from remote attacks. Private keys are safely stored through paper wallets together with offline computers that maintain complete isolation from data security threats.
The attractive aspect of vanity Bitcoin addresses from “Vanity BTC Address” requires users to exercise caution before implementation. Users generate bitcoin addresses through this method by designing them to display particular patterns or phrases for branding or personalization needs.
Vanity addresses contain security weaknesses because their key creation process is easily predictable. Hackers with advanced AI algorithms and supercomputing capabilities can use one of those tools to exploit the deterministic nature of vanity address generation and break into private key systems due to predictable patterns.
Security experts recommend the adoption of formalized and secure private key storage methods for crypto key protection against developing dangers and to maintain monetary asset integrity.
In a scenario where ancient, forgotten Bitcoin wallets resurface and encounter the formidable “AI Seed Phrase & Private Key Finder” program, the implications are profound and potentially perilous. This software, boasting unparalleled capability in decrypting crucial combinations of seed phrases and complete sets of private keys in remarkably brief spans, poses a significant threat to the security of dormant cryptocurrency holdings.
Imagine the dormant Bitcoin wallets, long consigned to oblivion by their owners, suddenly emerging into the spotlight. These wallets, once deemed lost beyond recovery, now face the stark reality of exposure to advanced artificial intelligence. With the “AI Seed Phrase & Private Key Finder,” the once-impenetrable fortresses guarding these digital assets appear alarmingly vulnerable.
Potential ScenariosUpon encountering this relentless decryption tool, several potential scenarios unfurl:
|
Implications for Cryptocurrency SecurityThe emergence of the “AI Seed Phrase & Private Key Finder” program signifies a paradigm shift in cryptocurrency security:
|
In essence, the convergence of long-lost Bitcoin wallets and the “AI Seed Phrase & Private Key Finder” program heralds a pivotal moment in the realm of cryptocurrency security. It underscores the imperative for stakeholders to remain vigilant, adapt to technological advancements, and fortify their defenses against ever-evolving threats.
USDT wallets represent the best solution to protect against hacker intrusions
People usually protect their digital assets by creating stronger barriers against malicious breaches in traditional approaches. The emergence of USDT wallets offers people a safer alternative to Bitcoin wallet vulnerabilities. The alternative wallet solutions defend against hacking attempts using AI and supercomputing and quantum computing thus delivering solid protection against malicious attacks.
Bitcoin suffers from inevitable hacking vulnerabilities that require immediate deployment of advanced protection methods. The evolution of cyber threats requires organizations to deeply analyze digital asset management strategies for achieving their best security outcome.
The growing sophistication of digital finance needs us to understand hackers remain advanced in their techniques because they develop methods that defeat standard security protocols and thus endanger your financial investments. Security measures based on quantum computing need immediate adoption because these systems possess the ability to decrypt supposedly secure encryption methods.
USDT wallets function as an effective security shield against hacker attacks. USDT delivers stronger privacy features along with stability benefits which make it attractive for users in the unpredictable market compared to Bitcoin’s public record system.
Why Use USDT Wallets:
- USDT wallets utilize enhanced security features that protect user assets through integrated advanced security measures and many wallets provide multi-signature capabilities as additional protection for cyber attackers.
- The USDT cryptocurrency functions as a Stable Value linked to the US Dollar which creates investment portfolios less susceptible to market volatility because it maintains steady prices for safer asset management without risk of sudden losses. The investment value of Tether stands as an essential product for investors.
- USDT wallets provide user-friendly management interfaces which streamline asset administration thus investors can invest strategically after they free up time from complex security protocol maintenance.
- USDT wallets connect effortlessly to decentralized finance (DeFi) platforms through which users can perform lending and stake their funds for yield farming while maintaining strong security practices.
United States Tether wallets function both as highly effective security storage and as forward-looking tools to protect digital assets effectively. Users enjoy two-factor authentication and decentralized identity features as standard features in these wallets which provide them with state-of-the-art security for their investments.