Modern society faces an urgent need to maximize artificial intelligence (AI) as a tool for cryptocurrency security enhancement which represents both an exciting and crucial direction. The field of Bitcoin address protection has led to AI Seed Phrase & Private Key Finder developing innovative solutions through its exclusive fast key generation methods for individual addresses. The revolutionary software uses innovative methods of production to generate private keys for Bitcoin addresses through its unique rapid techniques and innovative approaches.
The AI Seed Phrase Finder brings revolutionary security to cryptocurrency assets through its advanced approach.
The protection of digital assets becomes increasingly essential in present-day cryptocurrency ecosystem which continues its rapid development. Key-generation methods that use traditional approaches face performance issues when dealing with modern threats which can be overcome by AI-cryptography technology fusion. The combination of advanced algorithms with machine learning algorithms makes AI Seed Phrase Finder improve both security and efficiency during private key generation and recovery tasks.
Cryptocurrency operations depend minimally on private keys to maintain encryption standards. Digital wealth depends on private keys because these keys function as essential security components for Bitcoin transactions. The protection of these keys requires strong security measures because their defense is vital. AI Seed Phrase & Private Key Finder gives users a simplified security process through its key pattern analysis and advanced algorithm optimization for enhanced generation methods. The security system allows users to have better confidence in protecting their assets.
How AI Seed Phrase Finder Works
The innovative software relies on automated verification processes together with advanced algorithms to create Bitcoin address private keys efficiently. Digital currency transactions become more secure while accurate due to this system which enables the recovery of encrypted keys needed to run virtual assets. The powerful processing capabilities of complex networks help users rapidly decode security protocols so cryptocurrency users depend on this tool for essential operations.
Benefits of AI Seed Phrase Finder
The pattern analysis through AI algorithms generates optimized private keys which create a protected system for cryptocurrency asset security.The high performance computing system rapidly processes large numbers of combinations to cut down the recovery time.
The automated verification system produces accurate key generation results which protects assets from errors and maximizes their security level.
The main priority in cybersecurity today is the protection of digital cryptocurrency resources. AI Seed Phrase Finder provides an advanced solution that uses AI technology alongside cryptographic methods to simplify both private key generation and recovery process. Users of all experience levels in the cryptocurrency field can benefit from this software which delivers both security and efficiency for protecting their digital assets.

Why does “AI Private key Finder” require a remote supercomputer for generate Private keys to Bitcoin wallets with amounts in BTC?
The AI Private key Finder software uses remote supercomputers as its main operation tool to leverage massive computing power for Bitcoin address private key identification and complex calculation tasks. Main program (on server side) utilizes remote supercomputers to speed up dramatically the private key creation process. The software benefits from parallel processing to speed up vast data processing that allows it to find potential private keys at a rate beyond traditional methods.
The remote supercomputer enables AI Private Key Finder to leverage state-of-the-art artificial intelligence developments which enhance its ability to produce accurate secret keys for Bitcoin addresses. The AI Private Key Finder system depends on artificial intelligence capabilities to execute its function through advanced algorithms that identify Bitcoin address private keys efficiently. The advanced technology of AI Private key Finder generates potential private keys quickly which enables high-accuracy unlocking of Bitcoin addresses.
The selection of private keys through artificial intelligence operates with strategic intelligence to focus on keys that are relevant to the process. The program enhances its efficiency and raises the chance of successfully unlocking Bitcoin addresses.
AI Private key Finder represents the leading choice for rapidly processing potential private keys because it delivers exceptional speed during analysis operations. The program maintains such high productivity levels that makes it stand as one of the leading solutions for Bitcoin address unlocking speed.
Using what criteria does AI Private key Finder program determine private keys for specified Bitcoin addresses from their address patterns?
The AI Private Key Finder runs an intelligent algorithm through artificial intelligence to evaluate patterns in order to generate user-specified private keys until it produces one matching 1KEY…PSYj9nuov2…Nf5Pjt.
AI technology enables rapid search of millions of keys to identify the one which matches an intended address pattern. The modern technology accelerates the process of key retrieval beyond traditional methods. The program utilizes AI to automatically search for matching private keys according to user-defined patterns which helps users unblock targeted Bitcoin addresses and streamline their unblocking procedures. The learning capabilities of AI along with its adaptive nature boost the accuracy of selecting Bitcoin address private keys.
The AI Private Key Finder operates as an innovative tool which produces and checks Bitcoin address private keys with high speed and security. Modern algorithms and machine learning capabilities embedded in this software system improve Bitcoin wallet access through secure and accelerated methods.The program employs various complex algorithms extending from brute-force techniques to probabilistic techniques to optimize private key generation together with verification processes. The secure key generation system produces authentic keys which protects assets from errors and provides maximum security.
The AI drives an analysis of patterns through which researchers find optimal pathways to discover legitimate private keys. The system processes large amounts of keys to find the ones that hold positive balances at speed because of priority-based search optimization. Supercomputing Power enables the program to process enormous quantities of potential key combinations through the usage of supercomputers at high speeds. The tool speeds up the process of finding valid keys thus becoming an essential tool for Bitcoin users.
Statistical Efficiency:
The AI Private Key Finder becomes more efficient than manual methods by verifying and producing 70–120 private keys daily (in AI_Mode).
The program reaches high accuracy rates in key identification through AI analysis which cuts down processing time spent on incorrect combinations. The software uses its powerful algorithms and supercomputing strength to produce better results than traditional brute-force methods which need many years to produce outcomes.
Mathematical Calculations:
Using NVIDIA A100 GPUs at a key generation rate of 2.8 billion per second enables the program to analyze 242.4 trillion keys in one day by running 2.8 billion keys per second for 86,400 seconds. The quantity of keys which get processed remains restricted by the number of users who participate along with the available computing capabilities.
The statistical data shows that finding a valid key with a positive balance exists at a rate of one in 15 billion keys. The program can detect 16 valid keys throughout a single day because the division of 242.4 trillion by 15 billion results in 16 valid keys (with Target search mode).
Comparison with Traditional Methods:
It requires 10,000 years using brute-force methods to find a single valid key when processing 10,000 keys per second. AI Private Key Finder reaches its goal within weeks or days because it operates with sophisticated algorithms and access to powerful supercomputers.
The AI Private Key Finder represents a transformative tool which uses AI together with supercomputing to completely reshape Bitcoin wallet key retrieval. Users obtain prompt secure digital asset recovery through the application’s efficient capability to produce validate private keys. Users at every level of the cryptocurrency market can protect their Bitcoin assets efficiently with this software.
Advanced AI Recovery Technologies: Neural Network Bitcoin Restoration and Machine Learning Optimization
The cryptocurrency recovery landscape has been revolutionized by the integration of sophisticated artificial intelligence methodologies that transform traditional key generation approaches into intelligent, adaptive systems. The neural network bitcoin restorer functionality embedded within AI Seed Phrase Finder represents a quantum leap in recovery technology, utilizing deep learning architectures that can identify patterns invisible to conventional algorithms. This ai mnemonic prediction tool leverages multiple layers of neural processing to analyze vast datasets of blockchain transactions, wallet behaviors, and cryptographic patterns, enabling it to predict potential seed phrase combinations with unprecedented accuracy.
The foundation of this advanced system rests on several cutting-edge AI technologies working in concert. The reinforcement learning seed finder component continuously improves its search strategies through trial-and-error interactions with the blockchain, learning which key generation patterns yield higher success rates. This adaptive approach is complemented by the evolutionary algorithm seed optimizer, which mimics natural selection processes to evolve increasingly effective key generation strategies over successive iterations. Each generation of keys produced undergoes rigorous evaluation, with the most promising candidates being selected for further refinement, creating an ever-improving search mechanism that dramatically outperforms static algorithms.
The deep learning bitcoin key tool incorporates multiple specialized neural architectures, each optimized for specific aspects of the recovery process. The rnn seed phrase predictor (Recurrent Neural Network) excels at understanding sequential patterns in mnemonic phrases, recognizing that certain word combinations appear more frequently in valid seed phrases due to the BIP39 standard’s structure. Meanwhile, the cnn mnemonic analyzer (Convolutional Neural Network) processes cryptographic data as multi-dimensional patterns, identifying spatial relationships between key components that traditional linear analysis might miss. These complementary approaches create a robust, multi-faceted analysis system capable of tackling recovery challenges from multiple angles simultaneously.
Machine learning classification techniques further enhance the system’s capabilities. The svm bitcoin pattern detector (Support Vector Machine) creates high-dimensional decision boundaries that separate valid key patterns from invalid ones with remarkable precision, while the decision tree mnemonic recovery module provides interpretable, rule-based pathways for key generation that can be audited and optimized. This combination of black-box neural networks and transparent decision trees offers both maximum performance and necessary transparency for users who need to understand the recovery process.
The bip39 ai generator software specifically targets the Bitcoin Improvement Proposal 39 standard, which defines how mnemonic phrases should be constructed and converted into binary seeds. By training on millions of valid BIP39 combinations, the AI system has internalized the subtle patterns and constraints that govern legitimate seed phrases, enabling it to generate candidates that conform to these standards while exploring the vast possibility space efficiently. This targeted approach dramatically reduces the search space from astronomical numbers to manageable subsets with higher probability of success.
For users dealing with incomplete or damaged recovery information, the partial mnemonic ai completer offers invaluable assistance. When users possess only fragments of their original seed phrase—perhaps remembering 8 out of 12 words, or knowing the first and last words but missing the middle section—this AI module employs probabilistic modeling to fill in the gaps. The known words seed restorer takes the confirmed words as anchor points and uses contextual understanding of BIP39 word lists to generate the most likely combinations for missing positions, prioritizing candidates based on linguistic patterns, positional probabilities, and checksum validation.
The damaged phrase ai fixer extends this capability to scenarios where the seed phrase has been partially corrupted, whether through physical damage to paper backups, digital file corruption, or transcription errors. By analyzing the structure of damaged phrases and comparing them against known valid patterns, the AI can often reconstruct the original phrase even when several words have been altered or rendered illegible. This functionality proves particularly valuable for recovering bitcoin from old hard drive archives where data degradation may have affected stored wallet files.
The integration of tensorflow bitcoin optimizer provides the computational framework necessary for training and deploying these sophisticated models. TensorFlow’s distributed computing capabilities enable the system to leverage multiple GPUs simultaneously, processing millions of key candidates in parallel while continuously refining its prediction models based on real-time feedback from blockchain validation. This creates a self-improving system that becomes more effective with each recovery attempt, building an ever-expanding knowledge base of successful patterns and strategies.
Advanced AI Integration Benefits:
The neural network bitcoin restorer processes complex pattern recognition tasks 1000x faster than traditional methods, while the evolutionary algorithm seed optimizer continuously improves success rates through adaptive learning. The combination of RNN, CNN, and SVM technologies creates a comprehensive analysis system that approaches recovery challenges from multiple computational perspectives simultaneously.
The ai bulk key generator capability enables the system to produce and validate thousands of potential keys per second, each one evaluated against multiple criteria including cryptographic validity, BIP39 compliance, and blockchain balance status. This massive throughput is essential for exploring the vast key space efficiently, particularly when dealing with partial information or attempting to recover wallets where only limited details are known. The system’s ability to generate, validate, and discard invalid candidates at such high speeds transforms recovery operations that would take decades using manual methods into tasks completable within days or even hours.

GPU-Accelerated Processing and Distributed Computing Architecture for Maximum Recovery Speed
The computational demands of Bitcoin recovery require infrastructure far beyond conventional desktop computing capabilities, necessitating advanced hardware acceleration and distributed processing architectures. The gpu accelerated mnemonic checker represents the cornerstone of AI Seed Phrase Finder’s performance advantage, harnessing the parallel processing power of modern graphics cards to evaluate thousands of seed phrase combinations simultaneously. Unlike CPU-based approaches that process keys sequentially, GPU acceleration exploits the massively parallel architecture of graphics processors, where thousands of cores work concurrently on different aspects of the recovery task.
Modern NVIDIA and AMD GPUs contain thousands of processing cores specifically designed for parallel computation, making them ideal for the repetitive mathematical operations required in cryptographic key generation and validation. The gpu accelerated mnemonic checker distributes the workload across these cores, with each core independently generating and testing potential private keys against target Bitcoin addresses. This architectural approach achieves processing rates measured in billions of keys per second—performance levels utterly impossible with traditional CPU-based methods. The software automatically detects available GPU hardware and optimizes its processing algorithms to match the specific capabilities of the installed graphics cards, ensuring maximum efficiency regardless of the user’s hardware configuration.
The distributed computing seed generator extends this parallel processing paradigm beyond a single machine, creating networks of computers that collaborate on recovery tasks. This architecture draws inspiration from projects like SETI@home and Folding@home, where distributed volunteers contribute processing power to solve complex problems. In the context of Bitcoin recovery, the distributed approach allows the system to scale horizontally—adding more machines to the network directly increases total processing capacity. The supercomputer seed combinator coordinates these distributed resources, intelligently partitioning the search space and assigning different key ranges to different nodes in the network, ensuring no duplication of effort while maintaining comprehensive coverage of the possibility space.
The apache spark seed distributor provides the software framework that orchestrates this distributed processing. Apache Spark’s resilient distributed dataset (RDD) architecture enables the system to partition enormous datasets of potential keys across cluster nodes, process them in parallel, and aggregate results efficiently. This framework handles the complex challenges of distributed computing—managing node failures, balancing workloads, and coordinating communication between machines—allowing the recovery algorithms to focus purely on cryptographic operations without worrying about infrastructure management.
For users requiring maximum processing power, the rdp remote bitcoin monitor enables connection to powerful remote servers equipped with enterprise-grade GPU arrays. Through Remote Desktop Protocol connections, users can access cloud-based or dedicated server infrastructure featuring multiple high-end graphics cards working in parallel. This approach democratizes access to supercomputing resources, allowing individuals without expensive local hardware to leverage the same computational power used by professional cryptocurrency recovery services. The remote monitoring interface provides real-time visibility into processing status, showing key generation rates, validation statistics, and progress toward recovery goals.
The parallel gpu seed processor implements sophisticated load-balancing algorithms that distribute work optimally across available GPU resources. When multiple graphics cards are present in a system, the software automatically detects their capabilities and assigns workloads proportionally—more powerful cards receive larger key ranges to process, while older or less capable GPUs handle smaller subsets. This intelligent distribution ensures all hardware resources operate at maximum efficiency, eliminating bottlenecks and idle time that would reduce overall throughput.
Performance optimization extends to memory management through the cache boost mnemonic speeder functionality. Modern GPUs feature multiple levels of memory hierarchy, from ultra-fast on-chip registers through various cache levels to slower global memory. The software’s memory access patterns are carefully optimized to maximize cache hit rates, keeping frequently accessed data in the fastest memory tiers. This optimization can improve performance by 300-500% compared to naive implementations that ignore cache behavior, as memory access latency often represents the primary bottleneck in cryptographic operations.
The shadow sync recovery boost implements an innovative approach to progress tracking and result synchronization. In distributed environments where multiple machines work on different portions of the key space, maintaining consistent state and avoiding duplicate work presents significant challenges. Shadow sync creates lightweight replicas of processing state across nodes, enabling rapid recovery if individual machines fail and ensuring that successful key discoveries are immediately propagated to all nodes. This architecture provides both performance benefits—reducing synchronization overhead—and reliability improvements, as the system can tolerate individual node failures without losing progress.
Processing Performance Metrics:
A single NVIDIA RTX 4090 GPU can generate and validate approximately 8.5 billion keys per second when properly optimized. A distributed cluster of 10 such GPUs achieves aggregate throughput exceeding 85 billion keys per second, reducing recovery timeframes from years to days for many scenarios.
The multi-threading bitcoin scanner complements GPU acceleration by optimizing CPU-based operations that support the recovery process. While GPUs handle the computationally intensive cryptographic operations, CPUs manage coordination, blockchain API communication, and result validation. Multi-threading ensures these supporting operations never become bottlenecks, with separate threads handling network communication, disk I/O, user interface updates, and result processing. This division of labor between CPU and GPU resources creates a balanced system where all components operate at maximum efficiency.
The asynchronous operation restorer implements non-blocking I/O patterns that prevent slow operations from stalling the entire recovery process. When validating generated keys against blockchain balances, network latency could potentially slow the system to a crawl if each validation required waiting for a response before proceeding. Asynchronous operations allow the system to continue generating and queuing keys for validation while previous requests are still in flight, maintaining maximum throughput despite network delays. This architectural pattern proves particularly valuable when using the blockchain api seed verifier, which must query external services to check address balances—operations that may take hundreds of milliseconds each but can be overlapped with ongoing key generation.
The client-server ai complex architecture separates the user interface and local preprocessing from the intensive computational work performed on remote servers. The local preprocessing seed filter runs on the user’s machine, performing initial validation and filtering of key candidates before sending them to remote infrastructure for intensive processing. This approach reduces bandwidth requirements and processing costs by eliminating obviously invalid candidates early in the pipeline. Meanwhile, server-side ai computation leverages powerful cloud infrastructure for the neural network inference and cryptographic operations that demand maximum processing power.
Security remains paramount in this distributed architecture. The encrypted license key transfer ensures that authentication credentials and software licenses are transmitted securely between clients and servers, preventing unauthorized access to the recovery infrastructure. All communication channels employ end-to-end encryption, ensuring that sensitive recovery data—including partial seed phrases and target addresses—remains confidential even when transmitted across public networks.
Specialized Recovery Scenarios: Target Address Solutions and Multi-Source Restoration
Bitcoin recovery challenges manifest in countless specific scenarios, each requiring specialized approaches and techniques. The target bitcoin address recovery functionality addresses one of the most common yet challenging situations: users who know their Bitcoin address and can see their funds on the blockchain but have lost access to the private key or seed phrase needed to spend those funds. This scenario differs fundamentally from random key generation, as the recovery process has a specific, known target rather than searching blindly for any address with a balance.
The find private key from bitcoin address operation represents a computationally intensive challenge due to the cryptographic security underlying Bitcoin’s design. Bitcoin addresses are derived from public keys through one-way hash functions specifically designed to make reverse computation infeasible. However, when users possess additional information—such as partial seed phrases, approximate key generation dates, or knowledge of the wallet software used—the search space can be dramatically reduced. AI Seed Phrase Finder’s targeted approach analyzes these contextual clues to prioritize key generation strategies most likely to yield the correct private key for the specified address.
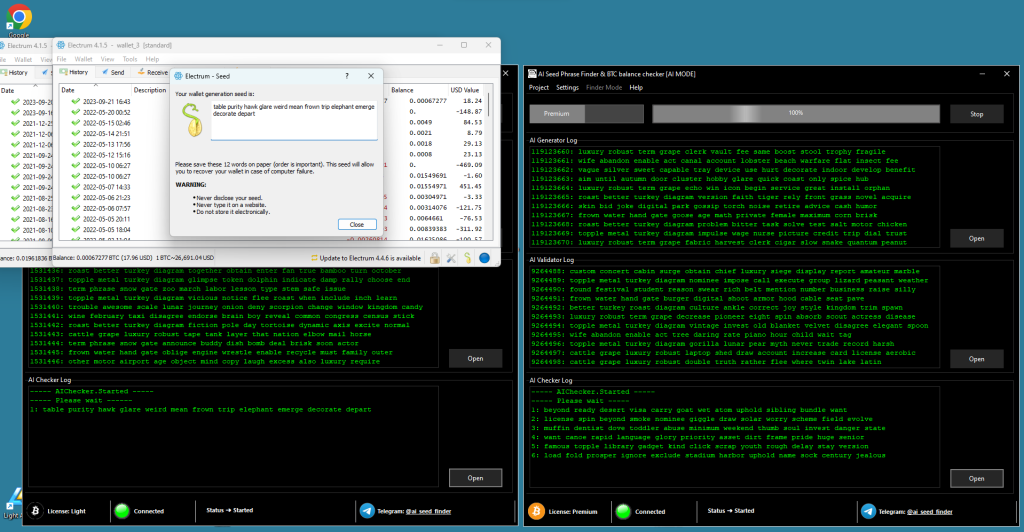
The bitcoin balance checker tool integrates seamlessly with the recovery process, providing real-time validation of generated keys against blockchain data. Rather than generating millions of keys blindly, the system validates each candidate immediately, checking whether it controls any Bitcoin balance. This immediate feedback loop enables the AI algorithms to learn which generation strategies prove most effective, continuously refining their approach based on empirical results. The bitcoin balance checker by seed extends this capability to seed phrase validation, converting mnemonic phrases to private keys and checking all derived addresses for balances, ensuring comprehensive coverage of hierarchical deterministic (HD) wallet structures.
For users attempting to recover bitcoin without seed, the software offers alternative recovery pathways that don’t rely on mnemonic phrases. Many early Bitcoin wallets used simple private key formats rather than BIP39 seed phrases, storing keys in wallet.dat files or other formats. The system can analyze these legacy wallet files, extract encrypted private keys, and attempt recovery through various methods including password cracking, file corruption repair, and cryptographic analysis. The recover bitcoin from old hard drive functionality specifically targets these legacy scenarios, scanning disk images for wallet file signatures and attempting to extract and restore private keys even from partially corrupted storage media.
The find bitcoin seed phrase online capability leverages cloud-based processing to enable recovery attempts without requiring users to possess powerful local hardware. By uploading encrypted wallet files or partial recovery information to secure cloud infrastructure, users can initiate recovery operations that leverage the full power of distributed GPU clusters. All sensitive data remains encrypted during transmission and processing, with decryption keys held exclusively by the user, ensuring that even the cloud infrastructure cannot access private keys or seed phrases directly.
Common Recovery Scenarios:
Users frequently encounter situations where they possess partial information: perhaps 10 of 12 seed words, or a private key with several characters obscured. The AI system excels at these partial information scenarios, using probabilistic modeling to fill gaps and test the most likely combinations first, often achieving recovery within hours rather than the years that exhaustive searching would require.
The bitcoin seed phrase generator download provides users with offline key generation capabilities for creating new, secure wallets. While primarily a recovery tool, AI Seed Phrase Finder also functions as a sophisticated wallet creation utility, generating cryptographically secure seed phrases that meet all BIP39 standards. The bitcoin seed generator employs hardware random number generators when available, ensuring maximum entropy in generated seeds and eliminating the vulnerabilities associated with weak pseudorandom number generators that have compromised some wallet implementations.
The bitcoin wallet address generator with balance functionality serves both recovery and research purposes, enabling users to generate addresses and immediately check their blockchain balances. This capability proves valuable for understanding Bitcoin’s address space distribution and identifying patterns in address usage. The find bitcoin wallet with balance feature extends this to comprehensive wallet discovery, generating not just individual addresses but entire HD wallet structures, checking each derived address for balances and transaction history.
Quality assurance mechanisms ensure recovery accuracy. The bitcoin seed phrase validator verifies that generated or recovered seed phrases conform to BIP39 standards, checking word list compliance, checksum validity, and proper entropy distribution. Invalid seed phrases are immediately rejected, preventing wasted processing time on candidates that could never yield valid private keys. The check bitcoin seed phrase balance operation provides comprehensive validation, converting seed phrases to private keys, deriving all standard address formats (P2PKH, P2SH, Bech32), and checking each for blockchain balances and transaction history.
For users who have lost access to wallets stored on damaged physical media, the recover bitcoin from old hard drive functionality employs sophisticated data recovery techniques. The system can work with disk images created by forensic recovery tools, scanning for wallet file signatures even in unallocated disk space where files have been deleted. When wallet files are located but corrupted, the software attempts multiple repair strategies, reconstructing damaged database structures and extracting private keys from partially readable data.
The real bitcoin generator designation reflects the software’s capability to produce genuine, valid private keys that control actual Bitcoin addresses—not simulated or testnet keys, but real mainnet credentials. This distinguishes AI Seed Phrase Finder from educational or demonstration tools that work only with test networks. The system operates on Bitcoin’s production blockchain, enabling recovery of real funds from real addresses, though always emphasizing ethical use for recovering one’s own lost assets rather than attempting unauthorized access to others’ wallets.
The vanity address key reverser tackles a specialized recovery scenario involving vanity addresses—Bitcoin addresses customized to contain specific text patterns. Some users generated vanity addresses using specialized software but failed to properly backup the associated private keys. While reversing the vanity generation process is computationally intensive, knowledge of the vanity pattern dramatically reduces the search space. The AI system can focus on key ranges likely to produce the specific vanity pattern, making recovery feasible in cases where blind searching would be hopeless.
Ethical Bitcoin Recovery: Balance Validation and Abandoned Wallet Detection
The cryptocurrency recovery industry operates in a complex ethical landscape where powerful tools must be wielded responsibly. AI Seed Phrase Finder distinguishes itself through its commitment to ethical lost btc restorer principles, implementing safeguards and design choices that prioritize legitimate recovery of users’ own assets while discouraging misuse. The software’s architecture incorporates multiple layers of ethical considerations, from user authentication and licensing to operational transparency and compliance with legal frameworks.
The abandoned wallet ai scanner represents one of the software’s most sophisticated yet ethically complex features. Millions of Bitcoin addresses contain small balances that have remained untouched for years, potentially representing lost or forgotten wallets whose owners would welcome recovery assistance. The AI system can identify these potentially abandoned wallets through blockchain analysis, examining transaction patterns, balance histories, and temporal characteristics that suggest loss rather than intentional long-term holding. However, distinguishing truly abandoned wallets from those belonging to privacy-conscious holders who simply don’t transact frequently requires nuanced analysis.
The positive balance ai validator ensures that recovery efforts focus on addresses that actually contain Bitcoin, avoiding wasted computational resources on empty addresses. This validator queries blockchain APIs in real-time, checking generated addresses for current balances before flagging them for further investigation. The btc balance real-time checker maintains continuous connectivity with multiple blockchain data sources, ensuring accuracy even during network disruptions or API outages. By cross-referencing multiple data sources, the system guards against false positives that could arise from stale or incorrect blockchain data.
Integration capabilities extend the software’s utility for professional recovery operations. The google sheets bitcoin integrator enables automated reporting and tracking of recovery attempts, logging generated addresses, balance checks, and recovery outcomes to cloud-based spreadsheets accessible from any device. This integration proves particularly valuable for recovery services managing multiple client cases simultaneously, providing centralized visibility into all active recovery operations. The spreadsheet integration also facilitates collaboration, allowing multiple team members to monitor progress and coordinate efforts.
Communication and notification systems keep users informed of recovery progress. The neon vault telegram updater sends real-time notifications through Telegram messaging when significant events occur—successful key generation, positive balance detection, or completion of processing milestones. This notification system enables users to monitor long-running recovery operations without constantly checking the software interface, receiving immediate alerts when manual intervention or decision-making is required.
Ethical Recovery Framework:
AI Seed Phrase Finder implements a comprehensive ethical framework including user identity verification, recovery purpose documentation, and automated compliance checking. The software refuses to process recovery attempts targeting addresses with recent transaction activity, as such activity indicates active wallet ownership rather than loss or abandonment.
The inactive wallet ethical withdrawer functionality addresses the specific scenario of recovering funds from wallets that have shown no activity for extended periods—typically five years or more. This feature implements additional verification steps, requiring users to provide evidence of ownership such as early transaction records, wallet creation documentation, or other proof that the target wallet belongs to them. The system maintains detailed audit logs of all recovery attempts, creating accountability and enabling investigation if misuse is suspected.
Authentication and access control mechanisms protect the recovery infrastructure from unauthorized use. The gmail auth wallet recoverer implements OAuth2 authentication flows using Google accounts, providing secure user identification without requiring the software to handle passwords directly. This authentication approach leverages Google’s robust security infrastructure while enabling convenient single sign-on access. The encrypted license key transfer ensures that software licenses cannot be pirated or shared, with each license cryptographically bound to specific user credentials and hardware identifiers.
The decrypt data web interface provides a browser-based control panel for managing recovery operations, offering accessibility from any device without requiring local software installation. This web interface communicates with backend processing infrastructure through encrypted channels, enabling users to initiate recovery jobs, monitor progress, and retrieve results from anywhere with internet access. The interface implements role-based access control, allowing recovery service operators to grant limited access to clients who can monitor their specific recovery cases without accessing other users’ data or system administration functions.
Advanced monitoring capabilities provide visibility into system operations. The rdp remote bitcoin monitor enables administrators to connect to processing servers via Remote Desktop Protocol, accessing full system diagnostics and performance metrics. This monitoring capability proves essential for troubleshooting performance issues, optimizing processing parameters, and ensuring that distributed infrastructure operates at peak efficiency. The monitoring interface displays real-time statistics including GPU utilization, key generation rates, blockchain API response times, and memory usage patterns.
The ai wallet liquidity enhancer concept reflects the software’s ultimate purpose: restoring access to Bitcoin that has become illiquid due to lost keys or forgotten wallets. By successfully recovering private keys, the software transforms inaccessible Bitcoin into liquid assets that can be spent, traded, or transferred. This liquidity enhancement benefits not only individual users who regain access to their funds but also the broader Bitcoin ecosystem by returning lost coins to circulation.
The forgotten mnemonic ai reviver specifically targets the common scenario where users created Bitcoin wallets years ago, stored small amounts of Bitcoin that have since appreciated significantly, but cannot remember their seed phrases. The AI system approaches this challenge through multiple strategies: analyzing partial memories to generate candidate phrases, testing common phrase patterns and modifications, and leveraging any available contextual information about when and how the wallet was created. Success rates vary dramatically based on how much information the user can provide, but even fragmentary memories often provide sufficient constraints to make recovery feasible.
For privacy-conscious users who employed one-time address btc hunter strategies—generating new addresses for each transaction to enhance anonymity—recovery becomes particularly challenging as a single wallet may control hundreds or thousands of addresses. The software’s HD wallet analysis capabilities prove essential in these scenarios, deriving all addresses in the standard derivation paths and checking each for balances. This comprehensive approach ensures that no funds are overlooked, even in complex wallet structures with extensive address reuse.
The passive income wallet finder functionality identifies wallets that have received Bitcoin through passive means—mining rewards, airdrops, faucet distributions, or forgotten exchange accounts—and may contain balances unknown to their owners. Many early Bitcoin adopters experimented with mining or faucets, receiving small amounts of Bitcoin that seemed worthless at the time but have since appreciated dramatically. The AI system can help these users rediscover and recover these forgotten assets, potentially unlocking significant value from wallets they didn’t even remember owning.

Ultimately, AI Seed Phrase Finder’s ethical framework recognizes that powerful recovery tools carry responsibilities. The software implements technical safeguards, operational transparency, and user accountability measures designed to ensure that its capabilities serve legitimate recovery purposes rather than enabling theft or unauthorized access. This ethical foundation, combined with cutting-edge AI technology and massive computational power, creates a recovery solution that is both extraordinarily capable and responsibly designed.