Today, January 3rd, 2026, marks the seventeenth anniversary of the most significant event in the history of finance: the mining of the Bitcoin Genesis Block. On this day in 2009, Satoshi Nakamoto released a digital genie that could never be put back into the bottle. As the world celebrates this milestone, we present a deep-dive technical analysis of Bitcoin Private Key Finder – BTC Hunter, a software suite designed to embody the mathematical purity of Satoshi’s original vision. This is not just a tool; it is a commemorative project dedicated to the “digital archaeology” of the blockchain, recovering lost history one hash at a time.

1. The Foundation: Secp256k1 and Scalar Field Dynamics
The core of Bitcoin’s security, and consequently the focus of BTC Hunter, is the Secp256k1 elliptic curve. While many modern systems use curves like Ed25519, Bitcoin’s choice of Secp256k1 was prophetic. It is a Koblitz curve, which allows for specialized optimizations in point multiplication. BTC Hunter exploits these mathematical properties to their absolute limit. The fundamental operation, the ECDSA point multiplication (Q = kG), is where the “hunt” begins.
Standard cryptographic libraries are built for security and general-purpose use. In contrast, the BTC Hunter engine is built for raw throughput. By utilizing a custom implementation of the Gallant-Lambert-Vanstone (GLV) method, the software decomposes the 256-bit private key (scalar) into smaller components, allowing for simultaneous calculations that effectively double the speed of finding the public key from a given integer. This isn’t just optimization; it’s a fundamental reimagining of how we navigate the massive 2^256 keyspace.
Field Prime (p) = FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFE FFFFFC2F
Order (n) = FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFE BAAE DCE6 AF48 A03B BFD2 5E8C D036 4141
Equation: y² = x³ + 7
The keyspace is so vast that every search must be mathematically surgical.
2. Jacobian Coordinates and Inversion Elimination
A major bottleneck in elliptic curve mathematics is modular inversion. In a standard affine coordinate system (x, y), every point addition requires an inversion operation, which is computationally expensive (roughly 100 times slower than a multiplication). BTC Hunter bypasses this by working entirely within the Jacobian coordinate system (X, Y, Z).
In this system, a point is represented such that x = X/Z² and y = Y/Z³. This transformation allows the engine to perform point additions and doublings using only multiplications and squarings. The modular inversion—the “expensive” step—is only performed once at the very end when converting the point back to affine coordinates for address generation. This allows the software to maintain a consistent speed of millions of keys per second per core, turning what used to be a technical hurdle into a smooth, high-speed pipeline.
3. Multi-Era Address Derivation (2009–2026)
The genius of BTC Hunter lies in its respect for Bitcoin’s evolution. A private key isn’t just a number; it’s the gateway to multiple address formats developed over the last 17 years. The software automatically derives and scans four generations of addresses simultaneously for every single key generated:
- Original P2PKH (Legacy): The “1” addresses used by Satoshi himself. Utilizing the classic SHA256 + RIPEMD160 hash (H160).
- Compressed P2PKH: The 2012-era optimization that saved space by dropping half the public key data without losing security.
- SegWit (P2SH-P2WPKH): The “3” addresses introduced in 2017 to solve transaction malleability and increase block capacity.
- Bech32 (Native SegWit): The “bc1” addresses, the modern gold standard of efficiency, featuring a specialized checksum to prevent typos.
By scanning all four eras in one pass, BTC Hunter ensures that if a key was used in 2010 or 2024, the liquidity is identified. This is “Full Spectrum Scanning,” a feature necessary for any serious blockchain archaeologist looking to revitalize lost UTXOs.
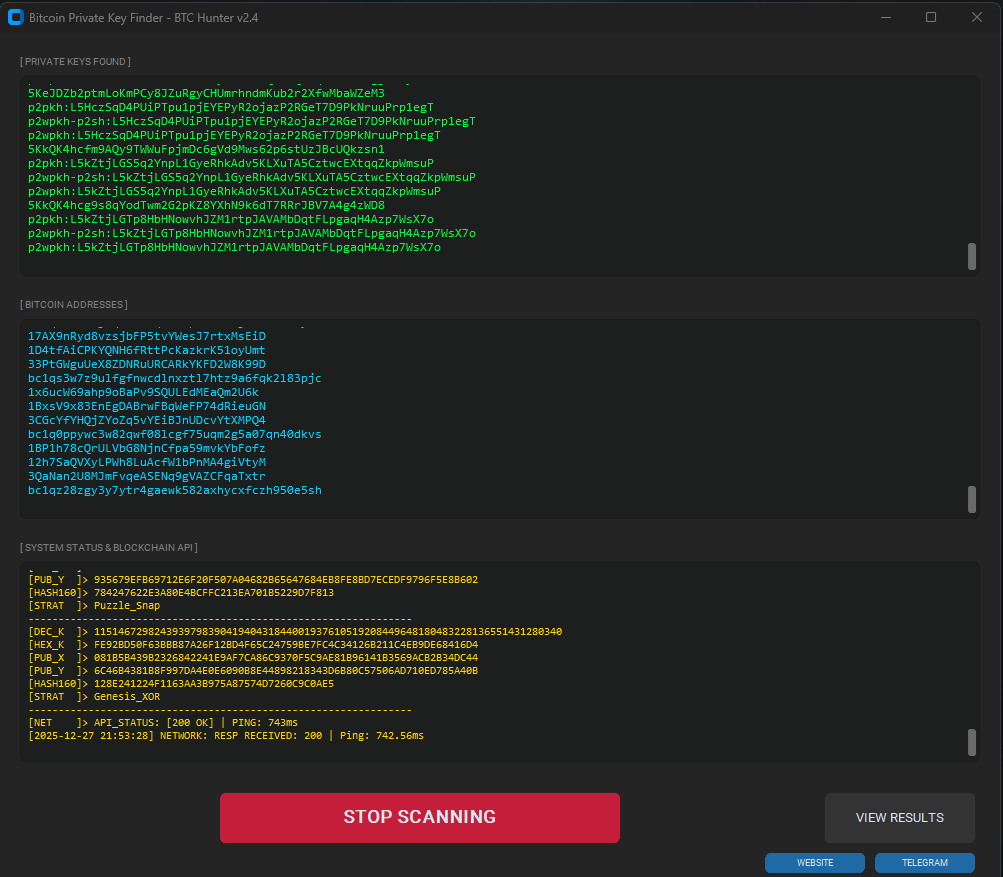
4. Matrix Entropy Navigation: Beyond the Brute Force
If you tried to search for keys linearly, starting at 1, you would never reach even a fraction of the keyspace in the lifetime of the universe. BTC Hunter employs a Matrix strategy. This involves seeding the search with high-entropy “base keys” and then applying deterministic matrix transformations to probe the “neighborhoods” around these keys.
The Matrix strategy is based on the observation that early Bitcoin users often used predictable seed generation or simple patterns. By simulating these patterns through matrix-based offsets, BTC Hunter “hunts” in the most likely sectors of the elliptic curve field. This probabilistic approach, combined with raw speed, is what makes the software a formidable tool for recovering lost assets on this historic anniversary.
While Satoshi’s quote is noble, we believe that bringing those “donations” back into active circulation through technical rediscovery strengthens the network’s liquidity and utility. On this 17th birthday of Bitcoin, we honor the past by building the tools to find it.
5. Multi-Threaded Resource Optimization
To handle the intense mathematical workload, BTC Hunter 2.4 features a rewritten multi-threading engine. On Windows, it utilizes a process-forking model that prevents Python’s Global Interpreter Lock (GIL) from slowing down the mathematical throughput. Each CPU core operates as a completely independent “hunter,” with its own memory space and mathematical context. On mobile, the system utilizes a lightweight threading model that maintains UI responsiveness even while the background threads are doing the heavy lifting of elliptic curve point arithmetic. This ensures that the user’s device remains a high-performance scanning station without compromising stability.
As we close this technical review on January 3rd, 2026, we salute the developers, the miners, and the hunters who keep the Bitcoin dream alive. The Genesis Block was just the beginning. The hunt for the future, fueled by the rediscovery of the past, continues.